1. draw a petri-net model representing the following workflow application. clearly label transactions and places. submission: petri net model in a pdf document.
Answers
The discrete interactions in a system are conceptually represented by finite state machines (FSM) and petri nets (PN).
One of the mathematical modeling languages for the description of distributed systems is the Petri net, often known as a place/transition (PT) net. It belongs to the discrete event dynamic system class. A Petri net is a directed bipartite graph with locations and transitions as its two types of members. White circles are used to represent place elements, whereas rectangles are used to represent transition elements.
Tokens, which are represented as black circles, can be found anywhere. If at least one token is present at every site connected to a transition as an input, the transition is enabled. According to some sources[1], Carl Adam Petri created Petri nets in August 1939 when he was just 13 years old in order to describe chemical reactions.
To know more about system click here:
https://brainly.com/question/27148473
#SPJ4
Related Questions
Online defamation occurs when an individual communicates a false statement about a person through the internet.
True False
Answers
Answer: true
Explanation: Online defamation occurs when an individual's reputation is injured by a false statement communicated by another person over the internet.
You would like to add some frequently used buttons to the quick access toolbar. How can you do this?.
Answers
Quick Access is a directory present in the Windows 11 File Explorer application. The purpose of the Quick Access section is to provide you with a list of recently or frequently opened files and folders and to help you easily get back to work. When you enable the Quick Access feature, you also get easy access to important folders like Desktop, Downloads, Documents, etc.
A feature similar to Quick Access used to be in older versions of Windows, which is the 'Favorites' section. Quick Access was first introduced in Windows 10. By default, the Quick Access feature is disabled in the File Explorer app in Windows, though, enabling it is quite simple.
You can learn more about Quick Access here brainly.com/question/23902602
#SPJ4
The registers are the communication channels inside the computer.( true or false)
Answers
Registers are storage, not channels
In project management, which step involves the project manager identifying
tasks needed to complete a project and the employees qualified to complete
them?
A. Planning
B. Executing
C. Initiating
D. Monitor
Answers
In project management, the step that involves the project manager identifying tasks needed to be completed and the employees qualified to complete them is known as Planning.
Project ExecutingProject Executing is the stage of project management where the project manager's plan is put into action.
At this stage, meetings are held, outlines are detailed and carried out, and everyone that should be involved in the task are contacted and assigned roles.
This stage involves identifying tasks and assigning them to employees qualified to carry out and complete the tasks.
Project managementIt is the application of processes, skills and knowledge to achieve specific project purposes
Therefore, the correct answer is option B.
Read more about project management here:
https://brainly.com/question/20070421
Isla is writing a report on the best roller coasters in America. Which device could help her with this?
Drone
Navigation system
Smart watch
VR headset
Answers
The device could help Isla with the above is VR headset.
What is a report?Report writing is known to ne a kind of formal style of writing a lot about a topic. People of report writing about a school event , Business, etc.
The device could help Isla with the above is VR headset because it will help her to be as if she is inside the roller coasters.
Learn more about writing a report from
https://brainly.com/question/192736
Show the following grammar is ambiguous, and give a corresponding unambiguous grammar. ::= ε | | ()
Answers
The given grammar is ambiguous, meaning that it allows for multiple interpretations of the same input. To address this ambiguity, an unambiguous grammar can be provided.
The given grammar is ambiguous because it allows for different parse trees for the same input. Let's consider the production rule ` ::= | ()`:
1. Using the production rule ` ::= ε`, we can generate an empty string.
2. Using the production rule ` ::= ()`, we can generate a pair of parentheses.
However, without any further rules or constraints, it is unclear how these two interpretations should be resolved. This ambiguity can lead to different meanings or interpretations of the grammar.
To provide unambiguous grammar, we can modify the original grammar by introducing separate production rules for an empty string and for a pair of parentheses. For example:
1. ` ::= ε`
2. ` ::= ()`
3. ` ::= ( )`
With this unambiguous grammar, the production rule ` ::= ε` generates an empty string, ` ::= ()` generates a pair of parentheses, and ` ::= ( )` generates a pair of parentheses enclosing another pair of parentheses.
By explicitly defining the different possibilities and their corresponding interpretations, the unambiguous grammar ensures that there is only one valid parse tree for each input, eliminating any ambiguity.
To learn more about grammar is ambiguous click here: brainly.com/question/31489465
#SPJ11
Fill in the blank: by negatively influencing data collection, ____ can have a detrimental effect on analysis.
Answers
By negatively influencing data collection, bias can have a detrimental effect on analysis.
What is bias?An error called bias in data happens when some components of a dataset are overweighted or overrepresented. Inaccurate representation of the use case by biased datasets results in biased results, systematic prejudice, and poor accuracy.
Therefore, A bias is an unbalanced preference for or opposition to an idea or object, usually in a way that is narrow-minded, discriminatory, or unfair. Biases can be acquired or innate. Biases for or against a person, a group, or a belief can develop in people. A bias is an intentional mistake in science and engineering.
Learn more about bias from
https://brainly.com/question/24491228
#SPJ1
In this unit, you learned that test generators can be very helpful when trying to determine if a code runs properly or fails in some situations. For example, let’s say that you were writing a program where the user would input their test grades and the program would tell them their average. What kinds of data would a test generator want to test for that program to be sure that it would work in all situations?
Answers
Answer:
Using boundary value analysis and assuming the valid range of test scores is [0 - 100],
min value, min value + 1-1 and 0A Nominal value between (0, 100)100 and 101max value - 1, max valueIn Boundary value analysis, we test the transition points where the program's behavior is expected to change. These transition points are the boundaries of valid and invalid partitions.
Min and max value are the smallest and largest possible values that you can store in your data type being used. This varies depending on the data type, so without knowing which you are using (and which language), I can't be more specific.
Need answer ASAP plz

Answers
Answer:
i can't read a single word on there i'll come back to it if you can zoom in a little
Explanation:
Write an LMC program as follows instructions:
A) User to input a number (n)
B) Already store a number 113
C) Output number 113 in n times such as n=2, show 113
113.
D) add a comment with a details exp
Answers
The LMC program takes an input number (n) from the user, stores the number 113 in memory, and then outputs the number 113 n times.
The LMC program can be written as follows:
sql
Copy code
INP
STA 113
INP
LDA 113
OUT
SUB ONE
BRP LOOP
HLT
ONE DAT 1
Explanation:
A) The "INP" instruction is used to take input from the user and store it in the accumulator.
B) The "STA" instruction is used to store the number 113 in memory location 113.
C) The "INP" instruction is used to take input from the user again.
D) The "LDA" instruction loads the value from memory location 113 into the accumulator.
E) The "OUT" instruction outputs the value in the accumulator.
F) The "SUB" instruction subtracts 1 from the value in the accumulator.
G) The "BRP" instruction branches back to the "LOOP" label if the result of the subtraction is positive or zero.
H) The "HLT" instruction halts the program.
I) The "ONE" instruction defines a data value of 1.
The LMC program takes an input number (n) from the user, stores the number 113 in memory, and then outputs the number 113 n times.
To know more about LMC program visit :
https://brainly.com/question/14532071
#SPJ11
an example of saas consumer is a company that uses the database servers provided by the cloud service provider to develop software applications. true false
Answers
'The given statement is true because SaaS (Software as a Service) is a cloud computing model where software applications are hosted by a third-party provider and made available to customers over the internet'.
In this model, the provider is responsible for maintaining the servers, databases, and infrastructure required to deliver the software application.A company that uses the database servers provided by a cloud service provider to develop software applications is a great example of a SaaS consumer.
This company can access the database servers and build their applications on top of it without having to worry about managing the underlying infrastructure. They can simply focus on developing their software application while the cloud service provider takes care of the hosting, security, and maintenance of the servers.Using SaaS solutions can provide companies with several benefits including lower costs, greater flexibility, and scalability.
In summary, the statement that an example of a SaaS consumer is a company that uses the database servers provided by the cloud service provider to develop software applications is true. SaaS provides companies with an easy and cost-effective way to access and use software applications without having to manage the underlying infrastructure.
For more such questions on Software as a Service visit:
https://brainly.com/question/14596532
#SPJ11
what are some scams you should avoid when looking for a credit counselor?
Answers
Before any credit counseling services are offered, the company requires money.
What exactly does a credit advisor do?Organizations that provide credit counseling can help you with your finances and bills, assist you with creating a budget, and provide training on money management. Its Fair Debt Collection Act's specific provisions have been clarified by the CFPB's debt recovery rule (FDCPA)
How is a credit counselor compensated?Non-profit organizations typically obtain some funding to cover their costs from two sources: clients who pay to use their debt payback program and clients' creditors who agree to cover those costs as part of the credit counseling organization's negotiated agreements with creditors.
To know more about credit counselor visit:
https://brainly.com/question/15563363
#SPJ4
What is climate and how is it formed? What can cause climate change.
Answers
Answer: Climate is the weather and conditions over time (at least a year).
The things that start climate change are burning fossil fuels and tearing down forests to start construction.
Answer:
climate can be defined as weather.
People who make money investing in the stock market.....
A) get certain tax breaks.
B) should sell quickly to avoid taxes.
C) have to pay a fee to keep a stock.
D) must pay taxes on profits.
The answer is D ^^^
Answers
Answer:
D must pay taxes on profits.
Explanation:
Consider the following code segment. int x = 1;while ( /* missing code */{System.out.print ( x + "" "");x = x + 2;
Answers
To complete the code segment, one needs to add a condition to the while loop. The condition will determine when the loop should continue iterating and when it should stop. This would result in the output: 1 3 5 7 9.
Based on the provided code snippet, it appears that the intention is to print the value of x and update its value by adding 2 in each iteration of the loop.
If one want to print the value of x until it reaches a certain threshold, such as 10, the missing code in the while loop condition could be:
while (x <= 10) {
System.out.print(x + " ");
x = x + 2;
}
With this code, the loop will continue executing as long as x is less than or equal to 10. In each iteration, it will print the current value of x, followed by a space, and then update x by adding 2. The loop will terminate when x exceeds 10.
This would result in the output: 1 3 5 7 9.
Leran more about the code segment here
https://brainly.com/question/28343520
#SPJ4
use divide-and-conquer approach to design an efficient algorithm that finds the contiguous subsequence with the maximum area in a given sequence of n nonnegative real values. analyze your algorithm, and show the results in order notation(big o). can you do better? obtain a linear-time algorithm. the area of a contiguous subsequence is the product of the length of the subsequence and the minimum value in the subsequence.
Answers
The maximum area of a contiguous subsequence in a given sequence of n nonnegative real values can be found using a divide-and-conquer approach.
First, we divide the sequence into two halves, left and right. Then, we recursively find the maximum area in each half.
To find the maximum area across the dividing point, we consider three cases:
1. The maximum area is entirely in the left half.
2. The maximum area is entirely in the right half.
3. The maximum area crosses the dividing point.
For cases 1 and 2, we can simply use the recursive result. For case 3, we expand the subsequence from the dividing point and find the minimum value in the subsequence. The area is then calculated as the product of the subsequence length and the minimum value.
This algorithm has a time complexity of O(n log n), where n is the number of elements in the sequence.
To obtain a linear-time algorithm, we can use a modified version of the Kadane's algorithm. This algorithm scans the sequence once and keeps track of the maximum area encountered so far. By updating the maximum area based on the current element and the previous maximum, we can find the maximum area in linear time.
The time complexity of the linear-time algorithm is O(n), which is more efficient than the divide-and-conquer approach.
Know more about contiguous subsequence, here:
https://brainly.com/question/6687211
#SPJ11
I WILL GIVE BRAINLIEST TO WHO ANSWERS FIRST AND CORRECTLY.
select all that apply
What guidelines should you follow when adding graphics to your presentations?
They should be used to make a bad presentation better.
Graphics should appear on each slide.
Graphics should only be used when they improve the communication.
Their size should be appropriate for viewing by your audience.
They should be relevant and appropriate to the content.
Answers
Answer:
Graphics should only be used when they improve the communication.
Their size should be appropriate for viewing by your audience.
They should be relevant and appropriate to the content.
Explanation:
Answer: 2 1 and 5
Explanation:
45 points!!!!!
One of the options for a software engineer is to work with the testing team of an SDLC project. In your view, state the pros and cons of placing a junior engineer with the testing team. Analyze it from both the company’s and employee’s points of view.
Answers
The pros and cons of placing a junior engineer with the testing team is that:.
The pros is that they get to learn.The cons is that one has to go back and try to explain things step by step which may slow down the project process.What are the pros and cons of a software engineer?The pros of a person as a software engineer are the fact that they gett paid well, they are often respected, and they have the freedom to work from home,
The cons or disadvantages is that they often feels stressed, overwork themselves and others.
Learn more about SDLC project from
https://brainly.com/question/26872062
identity the advantages and disadvantages of the types of computers
Answers
There are three sorts of computers based on their data handling capabilities: The analog computer. Computer that is digital. Computer hybrid. There are both benefits and drawbacks of using a laptop computer.
What are the benefits and drawbacks of computers?Nowadays, computers play an important part in human life. One of the most significant advantages of computers is their remarkable speed, which allows humans to complete tasks in a matter of seconds. The cost/stores are enormous - the amount of knowledge it is a coffee cost solution. A person can save a lot of data on a coffee budget. It is extremely speedy and allows us to do our work in record time. Stores Massive Datasets: Computers have the ability to store a significant amount of data. It is capable of storing files, documents, photos, and movies. Accur A disadvantage is defined as an unpleasant condition or something that puts someone in an undesirable situation.To learn more about computers, refer to:
https://brainly.com/question/21474169
#SPJ4
Write the steps of applying background colour to the document?
Answers
Answer:
Select add color
Explanation:
depends the program u are using
Please answer:
(Explanation is greatly appreciated).
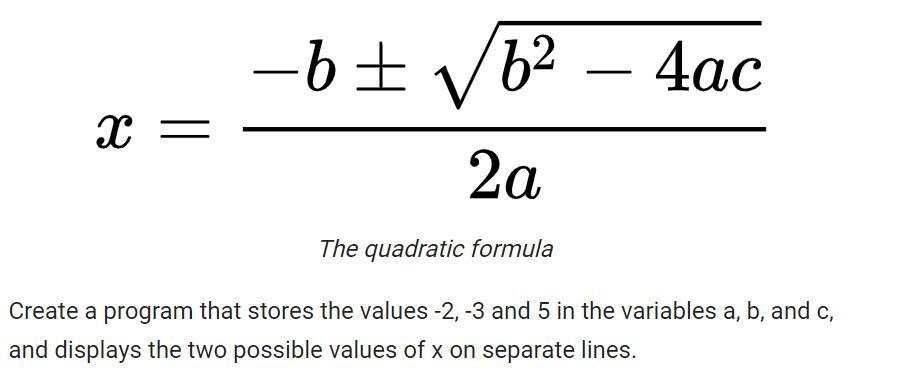
Answers
The c program for the given problem is as follows:
#include <stdio.h>
#include <stdlib.h>
#include <math.h>
int main(){
int a = -2; int b = 3; int c = 5;
double root1; double root2;
root1 = (-b - sqrt(b*b - 4*a*c))/(2*a); root2 = (-b + sqrt(b*b - 4*a*c))/(2*a);
printf("Root 1: %lf\n", root1);
printf("Root 2: %lf", root2);
return 0;
}
How the c program for this situation is built?The first step in building the program is inserting the libraries, which are:
#include <stdio.h> (standard for every program)#include <stdlib.h> (standard for every program).#include <math.h> (necessary due to the square root function).Then the coefficients of the formula can be declared with their values, as follows:
int a = -2; int b = 3; int c = 5;
The variables that will store the roots have to be declared, as follows:
double root1; double root2;
Then we apply the formula to calculate the roots, as follows:
root1 = (-b - sqrt(b*b - 4*a*c))/(2*a); root2 = (-b + sqrt(b*b - 4*a*c))/(2*a);
Then the roots are printed, as follows:
printf("Root 1: %lf\n", root1);
printf("Root 2: %lf", root2);
The \n clause inside the print guarantees that a new line is generated to print the second root.
Finally, the program is closed, as follows:
return 0;
}
A similar problem, also involving a c program, is given at https://brainly.com/question/15683939
#SPJ1
what is one important naming convention of functions?
Answers
One important naming convention of functions is to use descriptive and meaningful names that accurately represent the purpose or functionality of the function.
When naming functions, it is recommended to use clear and concise names that convey the intent and behavior of the function. This helps improve code readability and makes it easier for other developers to understand and use the functions. Good naming conventions also promote maintainability and reduce the likelihood of naming conflicts within the codebase.
Thus, using descriptive and meaningful names is the answer.
You can learn more about functions at
https://brainly.com/question/24846399
#SPJ11
A formula in cell D1 of this spreadsheet gives a result of 3. Which formula
was most likely entered in cell D1?

Answers
The duplicated formulas in cells G3 and E3 are =E3+F$3 and =$B3+D3, respectively. The contents of cell C1 will be 44, the value shown in cell E1 will be -40, and the result we will obtain is 7.
What does an Excel formula go by?Using specified values, referred to as inputs, in a given order, or structure, functions are established formulas that carry out calculations. Simple or sophisticated computations can be carried through using functions.
Which of the three formula kinds are they?Chemical formulas can be divided into three categories: empirical, molecular, and structural. Molecular formulas indicate the number of each type of atom in a molecule, empirical formulas display the simplest whole-number ratio of atoms in a compound, and structural formulas display the number of each type of atom in a compound.
To know more about cells visit:-
https://brainly.com/question/8029562
#SPJ1
Linux provides technology that allows the user to remotely view a graphical user interface and control mouse and keyboard events.Which of the following technologies establishes a connection with a remote computer using a viewer on one end and a server on the remote end? XRDP VNC SPICE
Answers
Answer:
I think it would probably be VNC
Explanation:
I have a linux, and it doesn't have the other two, and VNC is all about connections between computers.
Suppose that you have declared a numeric array named numbers, and two of its elements are numbers[1] and numbers[4]. You know that _________.
Answers
Answer:
there are exactly two elements between those two elements
which type of threat actor is an employee who wishes to personally ensure that the enterprise is exposed and blocked from accessing their customers' information until they ensure more secure protocols
Answers
An insider threat actor is an employee who wishes to personally ensure that the enterprise is exposed and blocked from accessing their customers' information until they ensure more secure protocols.
An insider threat is a malicious threat to an organization that comes from people within the organization, such as employees, former employees, contractors, or business associates. These actors have inside information concerning the organization's security practices, data, and computer systems.
They may use this information to gain unauthorized access to the organization's systems or data in order to steal, alter, or destroy information. Insider threats can be particularly damaging because these actors often have access to sensitive information and protocols that outsiders do not.
See more about insider threat at https://brainly.com/question/29708100.
#SPJ11
You are working from home and want to discuss a controversial topic. It is important you see the facial expressions of your coworkers during the meeting. The best way to conduct this meeting is using _______.
Answers
Answer:
Maintaing Focus and keeping the meeting comfortable and moving.
Explanation:
Answer:teleconference
Explanation:
♀️
How might an inventory of activities be different from an inventory of objects? *(I don’t understand this question. )*
Answers
I inferred you are referring to a business case, not computer and technology.
Explanation:
Put simply, an inventory of activities involves a record of the business routine activites such as last maintainance, last purchase of supplies etc.
However, the inventory of objects is diffrent as it records specifically how much inventory (objects; goods) a business have on hand.
In Python: Write a program to input 6 numbers. After each number is input, print the smallest of the numbers entered so far.
Sample Run:
Enter a number: 9
Smallest: 9
Enter a number: 4
Smallest: 4
Enter a number: 10
Smallest: 4
Enter a number: 5
Smallest: 4
Enter a number: 3
Smallest: 3
Enter a number: 6
Smallest: 3
Answers
Answer:
python
Explanation:
list_of_numbers = []
count = 0
while count < 6:
added_number = int(input("Enter a number: "))
list_of_numbers.append(added_number)
list_of_numbers.sort()
print(f"Smallest: {list_of_numbers[0]}")
count += 1
Part 1: Plan and Write the Pseudocode
Use the following guidelines to write your pseudocode for a fill-in story program.
1. Decide on a list of items the program will ask the user to input.
2. Your program should include at least four interactive prompts.
3. Input from the user should be assigned to variables and used in the story.
4. Use concatenation to join strings together in the story.
5. Print the story for the user to read.
Answers
Coding:
def main():
name = input("Enter your name: ")
age = input("Enter your age: ")
color = input("Enter you favorite color: ")
birth = input("Enter your birthday: ")
print(name + " is "+age+" year(s) old.")
print(name + "'s favorite color is "+color)
print(name + " was born on "+ birth)
main()
Explanation:
Pseudocode is a generic way of writing an algorithm, using a simple language (native to whoever writes it, so that it can be understood by anyone) without the need to know the syntax of any programming language.
