Each card in TigerGame is represented as an object of class Card. This class has three private member variables: rank (a value between 1-10), color (either purple or orange), and value, which is calculated as explained above. Use in-class initialization to initialize rank to 0, color to purple, and value to 0. Note that color is an enumerated type of type Color, which is added as a public member to Card.
Card has a parameterized constructor, which you will use to create an instance of each card in TigerGame (e.g., an orange card with rank 2). This constructor should initialize rank and color with the arguments provided and set value to its correct value given rank and color.
Card also has a function printCard() which must return a string in the following format:
color:rank. For example, for an orange card of rank 4 , printCard() should return orange:4.
The remaining three functions are getter functions to retrieve the values of the private member variables.
Card
rank: int
color: Color
value: int
+ enum Color {purple, orange}
+ Card()
+ Card(rank: int, color: Color)
+ printCard(): string
+ getRank(): int
+ getColor(): Color
+ getValue(): int
Answers
To implement the Card class in C++, you can use the following code:
#include <iostream>
#include <string>
class Card
{
public:
enum Color { purple, orange };
Card()
{
rank = 0;
color = purple;
value = 0;
}
Card(int rank, Color color)
{
this->rank = rank;
this->color = color;
this->value = (color == purple ? rank : 10 - rank);
}
std::string printCard()
{
std::string colorString = (color == purple ? "purple" : "orange");
return colorString + ":" + std::to_string(rank);
}
int getRank() { return rank; }
Color getColor() { return color; }
int getValue() { return value; }
private:
int rank;
Color color;
int value;
};
This code defines a Card class with the three private member variables rank, color, and value, as well as the public Color enumerated type. The class has a default constructor that initializes these member variables to default values, as well as a parameterized constructor that initializes the rank and color member variables with the provided arguments and calculates the correct value for the value member variable based on the rank and color.
The class also defines the printCard(), getRank(), getColor(), and getValue() functions, which provide the specified behavior for printing a card, as well as retrieving its rank, color, and value.
To Know More About C++, Check Out
https://brainly.com/question/23959041
#SPJ1
Related Questions
learning curves do have limitations. one key caution when using a learning curves is:
Answers
Learning curves have limitations, and one key caution when using them is ensuring the accurate representation of a specific learning process. They may not always accurately predict future performance or skill acquisition due to various factors.
A learning curve is a graphical representation of the relationship between experience and proficiency in a certain skill or process. As experience increases, individuals or organizations typically become more efficient and make fewer mistakes. However, learning curves have certain limitations that can affect their reliability.
One major limitation is that learning curves often assume a consistent rate of learning. In reality, the rate at which people learn can vary significantly depending on individual differences, learning methods, and the complexity of the task. Moreover, learning curves might not account for plateaus or periods of stagnation, where progress seems to halt temporarily before picking up again.
Another limitation is that learning curves might not consider external factors that can impact the learning process, such as changes in technology, resource availability, or market conditions. These factors can significantly influence the rate of learning and the eventual mastery of a skill or process.
In summary, when using learning curves to predict future performance or skill acquisition, it is essential to be cautious and aware of their limitations. They might not always provide an accurate representation of the learning process due to factors such as individual differences, the complexity of the task, and external influences.
To know more about the learning curves, click here;
https://brainly.com/question/10021119
#SPJ11
why does your computer need an operating system? list three to five reasons.
Answers
Answer:An operating system is a software which performs all the basic tasks like file management, memory management, process management, handling input and output, and controlling peripheral devices such as disk drives and printers
Explanation:
Your computer needs an operating system because of the following reasons:
The operating system regulates the memory of the computer along with its processes. The operating system authorizes you to communicate with the computer without knowing the actual language of the computer. It utilizes the complete set of resources occupied between the computer and the user. What do you mean by Operating system?An Operating system may be defined as a type of system software that significantly regulates computer hardware along with software resources. It also delivers some common services for processing computer programs.
The operating system controls the input instructed by the user to the computer with respect to the output delivered by the computer to the user. The function of the operating system always lies in this condition.
Therefore, the three ways by which your computer needs an operating system are well mentioned above.
To learn more about Operating systems, refer to the link:
https://brainly.com/question/1763761
#SPJ2
In Microsoft Windows 10,

Answers
Answer: Cancel all Print Jobs
Explanation: Whoever gave you this clearly doesn't know how to themselves cause the exact wording to cancel all print jobs is as follows
"Cancel All Documents". if this was a teacher tell them to read up on their technology skills before they give the next test. I'm currently working on my Master's in computer Programming and have been working with Computers for over 15 years. I could put a better multiple choice quiz together in less than 10 mins. I wonder how long it took this idiot to put that quiz together.
you are given two sequences a and b of n numbers each, possibly containing duplicates. describe an efficient algorithm for determining if a and b contain the same set of numbers, possibly in different orders. what is the running time of this algorithm?
Answers
Given are two sequences, S1 and S2, both with n items and possibly including duplicates. Efficient algorithm would be extremely wasteful to compare two sets of sequences if they were in some random order.
"A collection of finite rules or instructions to be followed in calculations or other problem-solving procedures" is what the word algorithm signifies. Or, "A finite-step process for solving a mathematical problem that frequently uses recursive operations."
As a result, an algorithm is a set of limited procedures used to solve a certain problem. Depending on what you want to do, algorithms might range from simple to sophisticated.
By using the process of making a novel recipe as an example, it can be understood. When following a new recipe, one must read the directions and carry out each step in the correct order. The new meal is cooked to perfection as a result of this procedures.
You employ algorithms every time you use a phone, computer, laptop, or calculator. Similar to this, algorithms assist programmers in carrying out tasks to produce desired results. The developed algorithm is language-independent, meaning that it consists only of simple instructions that can be used to build it in any language and still produce the desired results.
To know more about algorithm click on the link:
https://brainly.com/question/22984934
#SPJ4
what is definition of browser
Answers
"A web browser, or simply 'browser,' is an application used to access and view websites.
Explanation:
I hope It'll help you...
Answer:
a computer program with a graphical user interface for displaying and navigating between web pages.
Explanation:
compare and contrast the typewriter with that if the computer keyboard pls help omg
Answers
Answer:
Typewriters use paper and ink
and computers keyboards is an electroic typing
Explanation:
How do a router and switch differ when handling a message? Both a router and a switch use the message’s destination address to select the line to route the incoming message to. The switch will purposefully drop messages if message traffic exceeds its capacity. The router will purposefully drop messages if message traffic exceeds its capacity. There is no difference in how a router and a switch handle messages.
Answers
Answer:
The router will purposefully drop messages if message traffic exceeds its capacity.
Explanation:
As we know that the router and the switch are the connecting devices. The router works at the network layer and used for determining the shortest path
On the other hand the switch work is to connected many devices that are available in the network.
Therefore the correct option is second as the router also depicts when there is the purpose of the messaged drop[ed if the traffic of message exceeds than its capacity
Intro to CS edhesive 2.3 code practice question 2 answers
Answers

Answer:
ft=int(input("Enter the Feet: "))
inch=int(input("Enter the Inches: "))
ft2=int(input("Enter the Feet: "))
inch2=int(input("Enter the Inches: "))
fc=((ft + ft2)*12 + inch + inch2)//12
fc2=((ft + ft2)*12 + inch + inch2)%12
print("Feet: " + str(fc) + " Inches: " + str(fc2))
Explanation:
Got it right.
How does a cell phone change the
incoming signals from a caller into sound that
you can hear
Answers
Answer:
they send electrical signals to the buzzer. The buzzer changes those electrical signals into sound. You hear the buzzer sound and know that someone is calling you.
Explanation:
Answer: Cell phone or any electric device you can say changes the electric signal to radio waves at transmitting end which is converted back to electric signal and perceived as sound waves at receiving end
Explanation:
We use loops to: Process Numeric Data Ask users to enter information Repeat blocks of code Ask True/False questions
Answers
Answer:
Repeat blocks of code.
Explanation:
EXAMPLE JAVASCRIPT LOOP CODE
_________________________________________________________
INPUT:
while(true){//Check If bool True=True
console.log("Hello World!")
}
_________________________________________________________
OUTPUT:
Hello World!
Hello World!
Hello World!
Hello World!
Hello World!
\(\cdots\)
Hello World!
Hello World!
1. In the space below, explain how the Table Tools can be accessed in Word.
Answers
Answer:
Creating a Table
1) Click the Insert tab on the Ribbon
2) Click on Table
3) Highlight the number of columns and rows you’d like
OR
4) Click Insert Table
5) Click the arrows to select the desired number of columns
6) Click the arrows to select the desired number of rows
7) Click OK
Answer:
Click in the cell (or select multiple cells) that contains text you want to align. The Table Tools tab appears. Click the Layout tab under the Table Tools heading. … If you change the alignment of blank cells, any new text you type in those blank cells will appear according to the alignment you choose.
Explanation:
rubber sheet from discarded balloon
Answers
Answer:
so true
Explanation:
this is the prophecy me thinks
yo need help can someone plz help
You would like to search for information about storms but not tornadoes. What type of search strategy may be useful?
entering keywords into many different search engines
a Boolean search
a wild-card search
searching for synonyms
Answers
how many tutors have a status of temp stop? which tutors are active?
Answers
The exact number of tutors with a status of "temp stop" is not publicly available. However, tutors who are active can be identified by visiting the Tutors page on the Brainly platform. There, you will be able to view tutors who are currently active and available to answer questions.
Brainly is a platform that allows students to ask and answer questions related to their studies, and also to connect with tutors who can provide additional help. Tutors can have a status of either "active" or "temp stop." The exact number of tutors with a status of "temp stop" is not publicly available. However, active tutors can be identified by visiting the Tutors page on the Brainly platform. There, you will be able to view tutors who are currently active and available to answer questions. This is a useful tool for students who are looking for additional help with their studies.
Learn more about tutors: https://brainly.com/online-tutoring
#SPJ11
which line of java code correctly creates a two-dimensional array of integers containing six total locations (holds six numbers)?
Answers
To create a two-dimensional array of integers in Java containing six total locations, you can use the following line of code:
```java
int[][] myArray = new int[2][3];
```
This code creates a 2D array named "myArray" with 2 rows and 3 columns, resulting in a total of 6 locations to hold integer values.
An "array" is a data structure used to store a collection of elements of the same type. It provides a way to organize and access data in a sequential manner. Arrays are commonly used in programming and can be found in various programming languages. In an array, elements are stored in contiguous memory locations, and each element is identified by its index. The index represents the position of an element within the array, starting from 0 for the first element and incrementing by one for each subsequent element.
learn more about programming:https://brainly.com/question/23275071
#SPJ11
The protocol used to communicate network errors is known as __________.
Answers
Answer:
It is know as the ICMP, which means Internet Control Message Protocol, and is used to communicate errors back to the client
Explanation:
PLS HELP! Prompt
What is exporting?
Answers
Answer:
spread or introduce (ideas and beliefs) to another country.
Explanation:
Exporting is sending goods or services to another country for money. For example, Japan exported $16 million worth of mussels, meaning they sold $16 million worth of mussels to another country. Hope this helps!
true or false: on-site seo deals with the formatting of content on the website to maximize its chances of ranking for all desired searches.
Answers
On-site SEO deals with the formatting of content on the website to maximize its chances of ranking for all desired searches: True.
What is Search engine optimization (SEO)?Search engine optimization (SEO) can be defined as a strategic process which is typically used to improve and maximize the quantity and quality of the number of visitors (website traffics) that visits a particular website, by making it appear topmost among the list of results displayed by a search engine such as the following;
BingGoo-gleYah-ooThis ultimately implies that, search engine optimization (SEO) can help individuals and business organizations to maximize the amount of traffic that is generated by their website, through the strategic formatting of content on the website and placement at the top of the results returned by a search engine.
Read more on search engine here: brainly.com/question/27965856
#SPJ1
The average numbers of shares a piece of content receives is known as its:
Answers
Answer:
Amplification.
Explanation:
Social media publishing can be defined as a service that avails end users the ability to create or upload web contents in either textual, audio or video format in order to make them appealing to a target audience.
Thus, these web contents are generally accessed by end users from time to time through the use of various network-based devices. As users access these contents, they're presented with the option of sharing a particular content with several other people a number of times without any form of limitation.
Hence, the average numbers of shares a piece of content receives is known as its amplification. The higher the average numbers of shares a particular content receives, the higher the number of traffic it generates for its publisher.
suppose a program runs in 100 seconds on a computer, with multiply operations responsible for 80 seconds of this time. how much do we have to improve the speed of multiplication if we want my program to run four times faster? (calculate the improvement factor of multiplication
Answers
To make the program run four times faster, we need to improve the speed of multiplication by a factor of 4.
Given that the program runs in 100 seconds and multiplication operations take 80 seconds, we can calculate the current proportion of time spent on multiplication:
Current proportion of time spent on multiplication = Time taken by multiplication operations / Total program runtime
= 80 seconds / 100 seconds
= 0.8
To make the program run four times faster, we need to reduce the total runtime to one-fourth of the original time. Therefore, the desired total runtime is:
Desired total runtime = 100 seconds / 4
= 25 seconds
Now, we can calculate the desired time spent on multiplication operations by multiplying the desired total runtime with the current proportion of time spent on multiplication:
Desired time spent on multiplication = Desired total runtime * Current proportion of time spent on multiplication
= 25 seconds * 0.8
= 20 seconds
Finally, to calculate the improvement factor of multiplication, we compare the current time spent on multiplication (80 seconds) with the desired time spent on multiplication (20 seconds):
Improvement factor = Current time spent on multiplication / Desired time spent on multiplication
= 80 seconds / 20 seconds
= 4
To know more about program, visit:
brainly.com/question/30613605
#SPJ11
given a string matrix we in that need to find the
number which is occured two times or more than two times and and
give the sum of those numbers
Sample input::
[1 3 4
3 6 8
8 6 8]
Output:
3+8=11"
Plea
Answers
Given a string matrix, we need to find the number that occurred two times or more than two times and give the sum of those numbers. In order to do this, we can take the following approach:We can convert the string matrix into an integer matrix. We can create an empty dictionary. We will iterate through each element in the matrix.
If the element is not present in the dictionary, we will add it with the value 1. If the element is already present in the dictionary, we will increment its value by 1. After iterating through the matrix, we will iterate through the keys of the dictionary and add the sum of the keys whose values are greater than or equal to 2. The sum of these keys will be the desired output.
Here is the implementation of the above approach in Python: matrix = [[1, 3, 4], [3, 6, 8], [8, 6, 8]]d = {}# Convert string matrix to integer matrix for i in range(len(matrix)): for j in range(len(matrix[i])): matrix[i][j] = int(matrix[i][j])# Populate dictionary with occurrences of each number for i in range(len(matrix)): for j in range(len(matrix[i])): if matrix[i][j] not in d: d[matrix[i][j]] = 1 else: d[matrix[i][j]] += 1# Calculate sum of numbers that occurred 2 or more times sum = 0for key in d: if d[key] >= 2: sum += key print(sum) In the given problem, we have a matrix of strings and we need to find the numbers that occurred two or more times and sum them up. To solve this problem, we first need to convert the string matrix into an integer matrix. We then need to iterate through each element in the matrix and populate a dictionary with occurrences of each number in the matrix.
To know more about matrix visit:
https://brainly.com/question/29132693
#SPJ11
which two host names follow the guidelines for naming conventions on cisco ios devices? (choose two.)
Answers
RM-3-Switch-2A4* and SwBranch799* are the two host names follow the guidelines for naming conventions on cisco ios devices. The correct options are 2 and 3.
What is a host name?A hostname is a label assigned to a computer network connected device that is used to identify the device in various forms of electronic communication, such as the World Wide Web.
Hostnames can be simple single-word or phrase names, or they can be structured.
The two host names, RM-3-Switch-2A4 and SwBranch799, adhere to the guidelines for naming conventions on Cisco iOS devices.
Thus, the correct options are 2 and 3.
For more details regarding host name, visit:
https://brainly.com/question/13267319
#SPJ1
Your question seems incomplete, the missing part is attached below:

After establishing a long term goal and understanding what it entails, the best next step is
Answers
Answer:
plan numerous intermediate short-term goals.
Explanation:
help asap
In what way have the cells been connected?
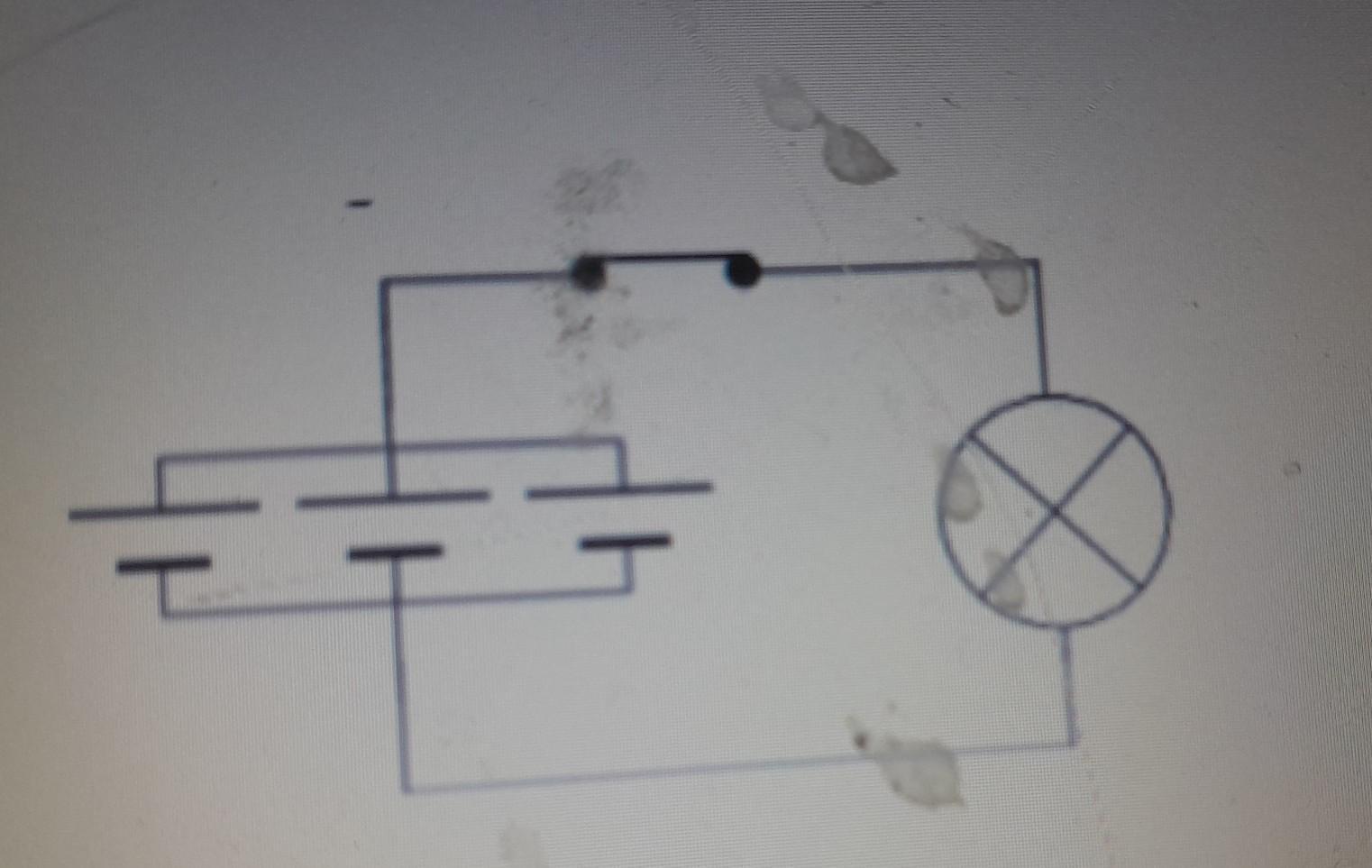
Answers
Based on the diagram, In 3 way the cells have been connected.
How are series-connected cells connected?When cells are coupled end to end so that the same amount of electricity must flow through each cell, they are said to be connected in series. Conversely, when cells are coupled positively to positively and negatively to negatively, they are connected in parallel, dividing the flow of current among the cells as 3 in the image.
Therefore, Multiple pathways connect the terminals in parallel combination circuits. All of the positive terminals of the cells are connected together, and all of the negative terminals are connected together in a parallel arrangement of cells.
Learn more about Parallel connection from
https://brainly.com/question/80537
#SPJ1
The Python language uses a compiler which is a program that both translates and executes the instructions in a high-level language.T/F
Answers
It is false that the Python language uses a compiler which is a program that both translates and executes the instructions in a high-level language.
What is compiler?A compiler is a computer software that converts computer code written in one programming language into another. A compiler is a specific software that converts the source code of a computer language into machine code, bytecode, or another programming language. Typically, the source code is written in a high-level, human-readable language such as Java or C++. A compiler is analogous to an interpreter. A compiler, on the other hand, is faster than an interpreter and can translate the entire file at once. Because an interpreter examines the original program line by line, it is a slower process. TurboC++ and Keil are two examples of widely used compilers.
Here,
It is incorrect that the Python language employs a compiler, which is a software that both interprets and executes high-level language instructions.
To know more about compiler,
https://brainly.com/question/4896128
#SPJ4
In what way, if any, does click-jacking differ from cross-site scripting?
They are essentially the same type of tricking people into using criminal websites.
They both direct people to criminal websites, but cross-site scripting misdirects URLs while click-jacking embeds code that
redirects a user.
They both direct people to criminal websites, but click-jacking misdirects URLs while cross-site scripting embeds code that
redirects a user.
O They both direct people to criminal websites, but users who engage in click-jacking know they are visiting criminal websites
Answers
Click-jacking differ from cross-site scripting as they both direct people to criminal websites, but click-jacking misdirects URLs while cross-site scripting embeds code that redirects a user.
The criminal practice of fooling a user into clicking on something other than what the user intends to click on is called click-jacking. Contrary to click-jacking, which uses the user as the confused deputy, cross-site request forgeries use the user's web browser. An other illustration of this kind of attack is an FTP bounced attack, which enables an attacker to make a covert connection to TCP ports that the target system is not allowed to access. The bewildered deputy in this illustration is the distant FTP server.
A computer program that is accidentally tricked by another party into abusing its power is known as a confused deputy. These attacks fall under the category of privilege escalation attacks. Cross-site request forgeries and clickjacking are two instances of the confused deputy issue.
To know more about click-jacking click on the link:
https://brainly.com/question/10742940
#SPJ4
your client has hired you to troubleshoot a network error. on inspection, it can be seen that the client has a static ip address, subnet mask, and default gateway all configured correctly. you open a browser to check the connection, and you can't get to a web page. you open a powershell window, ping the gateway, and ping 's public dns server, and everything is working. but you still can't navigate to websites. what kind of problem are you most likely to be experiencing?
Answers
Answer: Incorrect DNS
Explanation:
which of these analytics 360 features would you use to filter data and create a new data set for a specific use case or audience?
Answers
Sub properties is a tool in analytic 360 that allows to filter data and build a new data set suitable for a certain audience or use case.
What is the sub property?A sub property is an asset that gets its information from another asset. The facts in a sub property are generally (but no longer always) a subset of the facts in its supply assets.
To regulate, use sub properties. The user has access to information. Analytics 360 provides the tools and assistance that organizations require to get actionable insights from their data.
With Analytics 360, the team will have access to advanced tools such as Unsampled Reports and Data Driven Attribution, in addition to all of the standard Analytics capabilities and reports.
Therefore, it is sub properties.
Learn more about the sub properties, refer to:
https://brainly.com/question/10567185
#SPJ1
.The dirty (modify) bit identifies
A) a page that has been corrupted.
B) a page that needs to be reloaded when accessed.
C) a page that is shared by multiple processes.
D) a page that has been modified since it was loaded.
Answers
The dirty (modify) bit identifies: a page that has been modified since it was loaded since it was loaded into memory. Therefore, option D is correct.
The dirty bit, also known as the modify bit, is a flag that is associated with each page in a computer's memory management system. It is used to indicate whether a particular page has been modified (changed) since it was loaded into memory.
When a page is initially loaded into memory from secondary storage (such as a hard disk), the dirty bit is set to 0, indicating that the page is clean and has not been modified. However, when the contents of the page are modified by a process or program, the dirty bit is set to 1, indicating that the page has been modified.
The dirty bit is important for various memory management operations, such as page replacement algorithms and write-back policies. For example, when a page needs to be evicted from memory to make space for a new page, the operating system checks the dirty bit. If the dirty bit is set (1), it means that the page has been modified, and its contents need to be written back to secondary storage before it can be replaced. If the dirty bit is not set (0), it means that the page is clean, and it can be replaced without the need for writing it back.
The dirty (modify) bit is used to indicate whether a page has been modified since it was loaded into memory. It plays a crucial role in memory management operations, enabling efficient page replacement and write-back policies.
To know more about Memory, visit
https://brainly.com/question/14241634
#SPJ11
The overall appearance of goods and services can be trademarked.
True
False
Answers
Answer:
true
Explanation:
Will you mark me the brainest plz I will follow you