In order to make burger a chef needs at least the following ingredients: • 1 piece of chicken meat • 3 lettuce leaves • 6 tomato slices Write down a formula to figure out how many burgers can be made. Get values of chicken meat, lettuce leaves and tomato slices from user. Hint: use Python’s built-in function
Answers
Answer:
how many burgers would you have to make ?
Explanation:
this is a question ot an answer
Related Questions
How to do or create a shepard tone using additive synthesis in Pure Data. Please help, desperate!!
Answers
Answer:
Creating a Shephard Tone
Step 1: Choose a steady with constant pitch and volume and edit it to a 12 second long clip.
Step 2: Duplicate your track so that a copy plays simultaneously with your first.
Step 3: Statically pitch the entire duplicated clip down one full octave (or -12 semitones)
Which is an example of an operating system
a
Adobe Photoshop
b
Internet Explorer
c
Windows
d
Microsoft Word
Answers
Answer:
windows
Explanation:
Examples of Operating Systems
Some examples include versions of Microsoft Windows (like Windows 10, Windows 8, Windows 7, Windows Vista, and Windows XP), Apple's macOS (formerly OS X), Chrome OS, BlackBerry Tablet OS, and flavors of Linux, an open-source operating system.
. The total processing speed of microprocessors (based on clock rate and number of circuits) is doubling roughly every year. Today, a symmetric session key needs to be 100 bits long to be considered strong. How long will a symmetric session key have to be in 30 years to be considered strong?
Answers
Answer:
130 bits
Explanation:
If the length of a key = N bits
Total number of key combinations = \(\frac{2^{N} }{2}\)
For a key length of 100, the total number of key combinations will be \(\frac{2^{100} }{2} = 2^{99}\) combinations. This is a whole lot and it almost seems impossible to be hacked.
The addition of one bit to the length of the symmetric key in 1 year is sufficient to make the key strong, because even at double its speed, the processor can still not crack the number of combinations that will be formed.
Therefore, if a bit is added to the key length per year, after 30 years, the length of the symmetric session key will be 130 bits.
7d2b:00a9:a0c4:0000:a772:00fd:a523:0358 What is IPV6Address?
Answers
Answer:
From the given address: 7d2b:00a9:a0c4:0000:a772:00fd:a523:0358
We can see that:
There are 8 groups separated by a colon.Each group is made up of 4 hexadecimal digits.In general, Internet Protocol version 6 (IPv6) is the Internet Protocol (IP) which was developed to deal with the expected anticipation of IPv4 address exhaustion.
The IPv6 addresses are in the format of a 128-bit alphanumeric string which is divided into 8 groups of four hexadecimal digits. Each group represents 16 bits.
Since the size of an IPv6 address is 128 bits, the address space has \(2^{128}\) addresses.
which windows and network location enables network discovery and allows files and printers to be easily shared
Answers
The Private network location is the windows and network location enables network discovery and allows files and printers to be easily shared
How to determine the windowIn Windows, the organized area that empowers organize disclosure and permits simple sharing of records and printers is the Private network location.
After you set your arrange association to the Private network location, it empowers different arrange highlights, counting organize revelation, record sharing, and printer sharing.
By default, Windows categorizes arrange associations into three sorts:
PublicPrivateDomainThe Private network location is the foremost prohibitive, constraining organize disclosure and impairing record and printer sharing for security reasons.
Learn more about windows at: https://brainly.com/question/27764853
#SPJ1
I need help finishing this coding section, I am lost on what I am being asked.



Answers
Answer:
when cmd is open tell me
Explanation:
use cmd for better explanatios
Question 11
What type of program would have a class named Student with objects called fulltime and partTime?
Answers
What type of program would have a class named Student with objects called fullTime and partTime?
A. machine language program
B. object-oriented program
C. markup language program
D. procedural language program
Answer:
B. object-oriented program
Explanation:
An object-oriented program or OOP is a type of program that uses the concepts of objects and methods.
Although they are quite broad, they also make use of classes and types.
Java, for instance makes use of OOP as they use classes and objects under those classes and name them anyhow they want.
Therefore, the correct answer is B
Object-oriented Program.
We are told that;Class : students
Objects: Full time and part time.
This means the program is based on the concept of objects and Class. Now, from knowledge of programming, the one that deals with objects and Class is called Object-oriented Program.Examples of programming languages today that are object oriented are;
JavaScript, C++, and Python.
Where the program is used to structure software programs into simple, but also parts of code blueprints known as classes that are re-usable.Read more at; brainly.com/question/17148984
Which core business etiquette is missing in Jane
Answers
Answer:
As the question does not provide any context about who Jane is and what she has done, I cannot provide a specific answer about which core business etiquette is missing in Jane. However, in general, some of the key core business etiquettes that are important to follow in a professional setting include:
Punctuality: Arriving on time for meetings and appointments is a sign of respect for others and their time.
Professionalism: Maintaining a professional demeanor, dressing appropriately, and using appropriate language and tone of voice are important in projecting a positive image and establishing credibility.
Communication: Effective communication skills such as active listening, clear speaking, and appropriate use of technology are essential for building relationships and achieving business goals.
Respect: Treating others with respect, including acknowledging their opinions and perspectives, is key to building positive relationships and fostering a positive work environment.
Business etiquette: Familiarity with and adherence to appropriate business etiquette, such as proper introductions, handshakes, and business card exchanges, can help establish a positive first impression and build relationships.
It is important to note that specific business etiquettes may vary depending on the cultural and social norms of the particular workplace or industry.
Briefly explain the application of computer in your field of study.
Answers
Answer:
Computers are used to perform several tasks in industries like managing inventory, designing purpose, creating virtual sample products, interior designing, video conferencing, etc. Online marketing has seen a great revolution in its ability to sell various products to inaccessible corners like interior or rural areas.
Explanation:
Sam will be using several chemicals for processing photographic negatives and prints. What must he do before he uses darkroom chemicals?
А.thicken them
В.concentrate them
C.mix them together
D.dilute them
Answers
Answer:
dilute them
Explanation:
what member of an organization should decide where the information security function belongs within the organizational structure? why?
Answers
Answer:
Chief Information Officer (CIO) should be responsible for the overall management of information and data within the organization, and as such, is in the best position to understand the risks and vulnerabilities associated with this information.
The CIO can ensure that the information security function is able to effectively protect the organization's information and data, while also supporting the organization's business objectives.
Which of the following choices is not an example of a posible career in information technology
Answers
Compared to the remaining streams Networking systems is not an example of possible career in Information technology stream.
What is Information Technology?
Information Technology (IT) is the use of computers, storage, networks and other physical devices, infrastructure and processes to create, process, store, protect and exchange all forms of electronic data .
IT is generally used in the context of business operations rather than technology used for personal or recreational purposes.
Commercial use of IT includes both information technology and telecommunications
What is Networking systems?
Networking, also known as computer networking, is the transfer and exchange of data between nodes on a common information system medium.
To know more Networking systems visit:
https://brainly.com/question/27148473
#SPJ1
explain approaches of AI
Answers
Answer:
Main AI Approaches
There are three related concepts that have been frequently used in recent years: AI, machine learning, and deep learning.
Which of the following is an example of a
payload?
Answers
Answer:
LOAD
Explanation: PAY
Answer: it's B, E-Mail message
Explanation:
The ___ window is used to access all of the files and folders on the computer
Answers
The file explorer window is used to access all of the files and folders on the computer.
What is file explorer?
A built-in tool known as File Explorer may be used to examine and manage files and directories (called Windows Explorer in Windows Seven and earlier versions).
Click the File Explorer icon on the taskbar or double-click any folder on your desktop to launch File Explorer.
A new File Explorer window will be shown.
Learn more about File Explorer:
https://brainly.com/question/3902987
#SPJ1
Suggest how you would go about validating a password protection system for an application that you have developed. Explain the function of any tools that you think may be useful.
Answers
Use the drop-down menus to choose the file format that best corresponds to the video described.
your favorite band’s new music video:
the download of season 1 from a TV series
a pop vocalist’s music video posted online for purchase:
online streaming from a radio station:
Answers
The download of season 1 from a TV series: MKV (Matroska Video) is the best corresponds to the video described.
MKV (Matroska Video) is a popular video container format that is commonly used for storing high-quality video and audio files. It is a versatile format that can support various types of video codecs, audio codecs, and subtitle tracks.
When it comes to downloading TV series, MKV files are often preferred because they offer several advantages. Here are a few reasons why MKV is considered a good choice for TV series downloads:
Quality: MKV files can store video and audio in high quality without significant loss of data. They support various video codecs such as H.264, HEVC (H.265), and VP9, which are known for their efficient compression and excellent visual quality.
Learn more about visual quality on:
https://brainly.com/question/3466491
#SPJ1
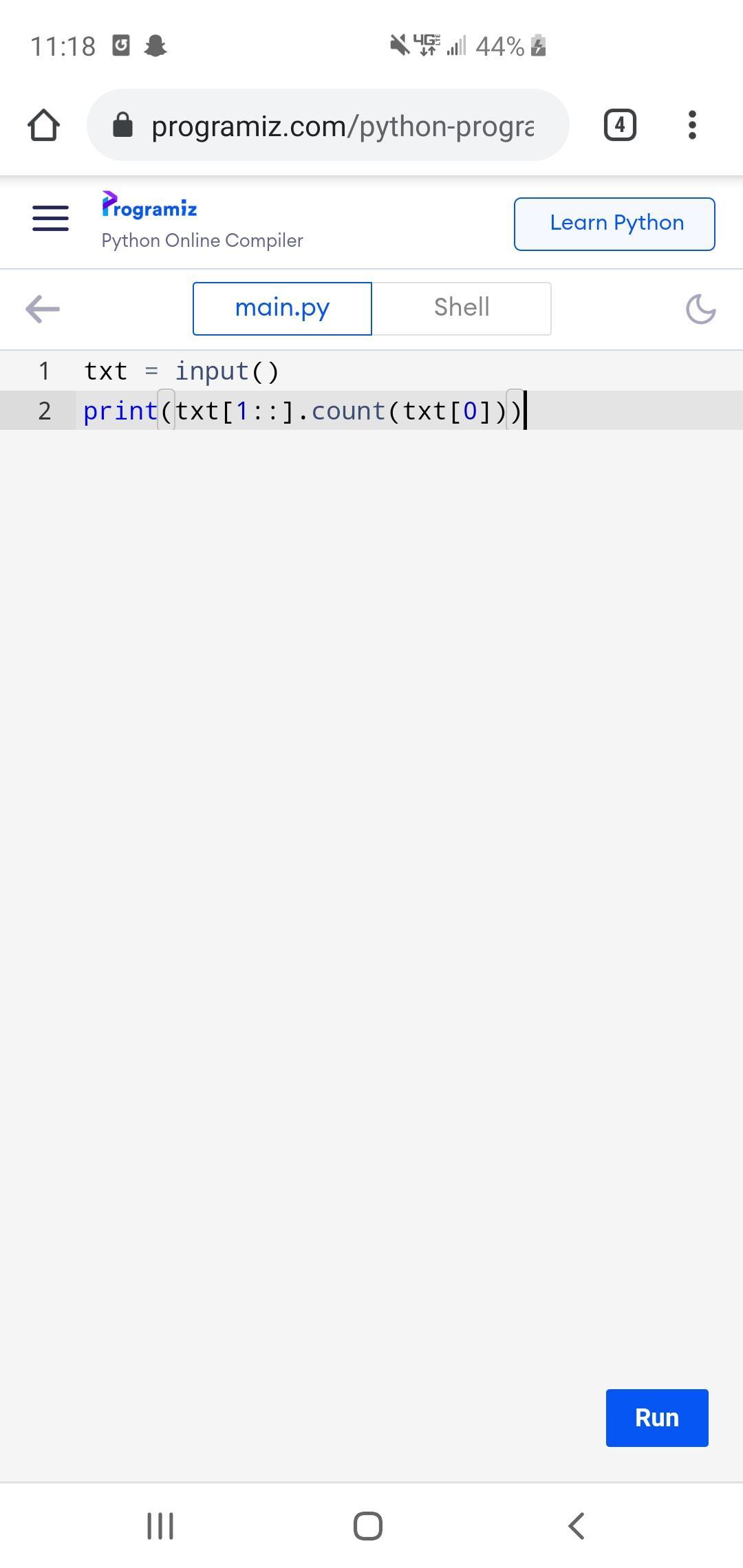
Write a program whose input is a string which contains a character and a phrase, and whose output indicates the number of times the character appears in the phrase.
Ex: If the input is:
n Monday
the output is:
1
Ex: If the input is:
z Today is Monday
the output is:
0
Ex: If the input is:
n It's a sunny day
the output is:
2
Case matters.
Ex: If the input is:
n Nobody
the output is:
0
n is different than N.
Learning Python
Answers
Explanation:
1
Ex: If the input is:
z Today is Monday
the output is:
0
Ex: If the input is:
n It's a sunny day
the output is:
2
Case matters.
Ex: If the input is:
n Nobody
the output is:
0
n is different than N.
Learning Python
I've included my code in the picture below. Best of luck.
The groups within a tab are collectively
known as?
Answers
Answer:
the ribbon
Explanation:
Commands are organized in logical groups, which are collected together under tabs. Each tab relates to a type of activity, such as formatting or laying out a page. To reduce clutter, some tabs are shown only when needed.
Which is an example of a loan secured by collateral?
A.Jama charged $2000 on her credit card for a vacation to Mexico.
B.Trey secured a $2000 loan to pay his college tuition.
C.Jorge secured a loan for $2000 from his uncle.
D.Joyce paid $2000 in downpayment and secured a loan on a new car.
Answers
An example of collateral can be Joyce's downpayment of $2000, to the bank in order to secure the loan for a new car. Thus, option D is correct.
What is collateral?Collateral has been given as something that is placed in terms of security in the time of granting loans and in the case of default payment it can be fortified.
The collateral can be in varying terms such as real estate collateral, business equipment collateral, and inventory collateral. cash collateral and many others, The importance of collateral have been to reduce the risk of the banks, in case of default when the business is unable to pay back the loan.
An example of collateral has been a downpayment made by Joyce of amount $2000, in order to secure the loan for the new car. Thus, option D is correct.
Learn more about collateral, here:
https://brainly.com/question/6779619
#SPJ5
You are given an initially empty queue and perform the following operations on it: enqueue (B), enqueue (A), enqueue(T), enqueue(), dequeue(), dequeue(), enqueue (Z), enqueue(A), dequeue(), enqueue(1), enqueue(N), enqueue(L), dequeue(), enqueue(G), enqueue(A), enqueue(R) enqueue(F), dequeue), dequeue(). Show the contents of the queue after all operations have been performed and indicate where the front and end of the queue are. Describe in pseudo-code a linear-time algorithm for reversing a queue Q. To access the queue, you are only allowed to use the methods of a queue ADT. Hint: Consider using an auxiliary data structure.
Answers
Reversing a queue Q in linear time: ReverseQueue(Q): stack = []; while Q: stack.append(Q.pop(0)); while stack: Q.append(stack.pop()).
After performing the given operations on the initially empty queue, the contents of the queue and the positions of the front and end of the queue are as follows:
Contents of queue: T Z 1 A G A R F
Front of queue: points to the element 'T'
End of queue: points to the element 'F'
To reverse a queue Q in linear time, we can use a stack as an auxiliary data structure. The algorithm will work as follows:
Create an empty stack S.Dequeue each element from the queue Q and push it onto the stack S.Once all elements have been pushed onto the stack S, pop each element from the stack S and enqueue it back onto the queue Q.The elements of the queue Q are now in reversed order.Pseudo-code for the algorithm is as follows:
reverseQueue(Q):
create a stack S
while Q is not empty:
x = dequeue(Q)
push(S, x)
while S is not empty:
x = pop(S)
enqueue(Q, x)
This algorithm reverses the order of the elements in the queue in linear time O(n), where n is the number of elements in the queue.
Learn more about algorithm here:
https://brainly.com/question/17780739
#SPJ4
What is Memory Card? Explain?
Answers
A memory card is basically a card that holds memory. The card can be removed at anytime and put into any other device. It is mainly used for extra storage and to transport videos, pictures, etc. to other devices
Hope this helps. : )
assume that the variable teststring refers to a string. write a loop that prints each character in this string, followed by it's ASCII value
Answers
Answer:
Explanation:
The program and the result of its execution:

What is the output for the following code? Enter the result in the blank.
>>> num = "abcdefghi"
>>> num[2:5]
Answers
Answer:
Cde
Explanation:
Because if you look at abcdefghi, In programming you start with 0. So it would be a:0 b:1 c:2 d:3 e:4 f:5 g:6 h:7 i:8. So if you say 2:5, it would be from c to e. Because in programming you dont count the last letter which is 5 you use the letter right before 5 to end it. Sorry its a bit confusing. But im 100% sure its right.
Answer:cde
Explanation:this is the correction on odyssey!!
What is a complier in computers
Answers
Answer:
Explanation:
A compiler is a computer program that translates source code into object code.
1
2
3
4
5
How do simulators react to the actions of the user?
Consequences happen on a delay, and then explain what the user has done right or wrong.
O Consequences are immediate and the user may need to further act or respond.
O Consequences are quick, and then the user must move into the next program.
O Consequences do not happen unless the user has done something incorrectly.
Answers
Consequences in simulators can vary depending on the type of simulator being used. However, in general, consequences are often immediate or happen on a short delay.
What is the simulators?The simulator may provide feedback to the user on what they have done right or wrong, and the user may need to further act or respond based on that feedback. In some cases, consequences may be delayed in order to allow the user to see the full impact of their actions.
It is also possible for consequences to not occur unless the user has done something incorrectly, but this would depend on the specific design of the simulator.
Option A is the most accurate answer. Simulators typically react to the actions of the user with a delay, and then provide feedback on what the user has done right or wrong. This allows the user to learn from their actions and make adjustments in the future.
Learn more about simulators from
https://brainly.com/question/28940547
#SPJ1
Readable code
1. is written in large font.
2. is written neatly in straight columns.
3. is easy to understand and useful to other programmers working with the code.
4. is password protected so that only authorized programmers can access it.
Answers
Answer:
Readable code is easy to understand and useful to other programmers working with the code, or C on Edge.
Explanation:
It's in the notes on edge in the "Readible Code" section
Readable code is code that is well-structured, commented, and easy to understand, making it useful to other programmers working with the code. Therefore, the correct answer is option C.
The most important part of writing readable code is making sure it is well-structured and easy to understand for other programmers. This means using consistent formatting such as clear indentations, consistent naming conventions, and including comments to explain logical operations. Additionally, making sure the code is written in a large font so that it is not too small can be helpful in improving readability. Finally, password protecting the code so only authorized programmers can access it can help prevent tampering and unauthorized modifications.
Therefore, the correct answer is option C.
Learn more about the readable code here:
https://brainly.com/question/19540657.
#SPJ2
y library> COMP 107: Web Page Design home > 49. LAB Auto loan (CSS) Students: Section 4.9 is a part of 1 assignment Week 7 LAB: Auto Loan (CSS) 4.9 LAB: Auto loan (CSS) Create an external stylesheet so the provided HTML produces the following web page Comparison of Dealer Incentives and Loan Offers Purchase Offer 1 Purchase Offer 2 am Cost Purchase price $33.500 Purchase price Cash incentive rebate $0 Cash incentivebate Loan term (months) 48 Loan term (mores Annual percentage rate (APR) 32 Annual porcentago (APS) Monthly payment 572530 Monthly payment search D O 方 E
Answers
This lab requires that you create an external stylesheet to style the web page. You should include elements such as font size, font family, font weight, font style, font color, background color, background image.
What is the elements?Elements are the basic substances that make up all matter in the universe. They are the fundamental building blocks of all matter and are made up of atoms. There are currently 118 known elements, including hydrogen, oxygen, carbon, nitrogen, and iron. Elements are organized on the periodic table according to their chemical and atomic properties. They are classified by their atomic number, number of protons, and chemical properties. When elements combine, they form compounds, which can have properties that are different from the elements that make them up.
To learn more about elements
https://brainly.com/question/29338740
#SPJ1
how can a security framework k assist in the deisng and implementation of a secuiry infrastructure what isn information security governance
Answers
Answer:
on January 1st the new year begins rewrite and punctuate correctly
Which part of the Result block should you evaluate to determine the needs met rating for that result
Answers
To know the "Needs Met" rating for a specific result in the Result block, you should evaluate the metadata section of that result.
What is the Result blockThe assessment of the metadata section is necessary to determine the rating of "Needs Met" for a particular outcome listed in the Result block.
The metadata includes a field called needs_met, which evaluates the level of satisfaction with the result in terms of meeting the user's requirements. The needs_met category usually has a score between zero and ten, with ten implying that the outcome entirely fulfills the user's demands.
Learn more about Result block from
https://brainly.com/question/14510310
#SPJ1