In some ways a compressor is the opposite of a Gate. Which of these applies to a compressor?
Answers
In some ways a compressor is the opposite of a Gate, dynamic range of an audio signal applies to a compressor.
A compressor is the opposite of a gate. A compressor applies to the process of reducing the dynamic range of an audio signal, whereas a gate is designed to mute or attenuate a signal when it falls below a certain threshold. In essence, a compressor works to manage the loud parts of a signal, while a gate controls the quieter parts.
The ratio between the greatest and lowest values that a particular variable can assume is known as the dynamic range (abbreviated DR, DNR, or DYR). It frequently refers to signs like sound and light.
Learn more about the compressor and gate at brainly.com/question/14145208
#SPJ11
Related Questions
Which is used to input information on a laptop?
Answers
Answer:
The keyboard.
Explanation:
You use the keyboard to input info in a computer.
Dan's team has to develop billing software for a supermarket. During which step will they write the program for the software?
Which step will involve finding errors in the software?
Answers
Answer:
coding phase
testing/debugging phase
Explanation:
During the coding phase they will write the actual code which creates the functionality/program which is added to the software. This phase comes after the dev team designs the algorithm and creates a flow chart of the algorithm. This flow chart is what is used to create the code itself. After the code is complete then the dev team will go into the testing/debugging phase where they will test the program with different test cases. If any bugs/errors are found they will return to the code and implement changes to fix these errors.
Start from vertex A, use Prim's algorithm to find a minimum spanning tree (MST) for the following weighted graph: Show the weight of the MST, the sequences of the edges added to the MST during the construction and draw the MST.
Answers
Once I have that information, I can guide you through Prim's algorithm to find the minimum spanning tree (MST) and provide the weight of the MST, the sequence of edges added, and draw the MST.
what is the weight of the minimum spanning tree (MST), the sequence of edges added, and the corresponding drawing for the given weighted graph?To demonstrate Prim's algorithm for finding a minimum spanning tree (MST), I'll need the weighted graph with the edge weights.
Please provide the weighted graph with its corresponding edge weights, and I'll be happy to guide you through the algorithm step by step, including the weight of the MST, the sequence of edges added, and the drawing of the MST.
Learn more about weight
brainly.com/question/31659519
#SPJ11
Which unit of binary storage has a size that is processor dependent?.
Answers
It should be noted that the unit of binary storage has a size that is processor dependent is word.
What is binary storage?In a binary storage , all the information that is been stored in a computer is usually done by following a sequence of 0's and 1's, .
Since the storage devices consist of a set of locations and do have one of two possible states.
learn more about binary storage at;
https://brainly.com/question/21400963
Why is manual coding the best way to learn HTML?
You can look at source code and figure out how markup affects function.
You can sometimes drag-and-drop pieces of content.
You can apply styles to text as you would with a word processor.
There are many formatting shortcuts to choose from.
Answers
Answer: A: You can look at source code and figure out how markup affects function.
Explanation: I did research on it, using credible sources.
Answer:
A
Explanation:
I did it edge 2021
b. 2 and 22
function,
13. To input a decimal you need the
a. float
b. int
C. str
d.
val
Python
Answers
Answer:
i think the answer is c so yea
Page layout was initially used in desktop publishing (DTP), but is now commonly used to describe the layout of webpages as well. a. True b. False
Answers
Page layout: This technique is used to develop publications with a more unique layout, such as newsletters, books, or posters. Similar to a canvas, a page layout document lets you add text boxes, photos, and other objects before arranging them anyway you like on the page.
What is the desktop publishing (DTP) used in page layout?Initially used almost solely for print publications, it is now also utilized to help create a variety of online content types.
Therefore, The positioning of text, graphics, and other elements on a page is referred to as page layout. Although it was originally meant to explain desktop publishing (DTP), the phrase is now frequently used to describe how websites are laid out.
Learn more about page layout here:
https://brainly.com/question/9234021
#SPJ1
Answer:
true
Explanation:
How can Mario complete his task without leaving the word application?
Answers
Answer:Use the Thesaurus feature to find a synonym of the word.
Explanation:i just got the same question.
Answer:Use the Thesaurus feature to find a synonym of the word.
Explanation:
what type of data structure associates items together?
A. binary code
B. dictionary
C. interface
D. editor
Answers
The type of data structure associates items together is dictionary.
A dictionary, additionally known as a map or associative array, is the structure of a record that shops statistics in key-price pairs. It permits green retrieval and manipulation of data by associating a unique key with each price.
In a dictionary, the key serves as the identifier or label for a selected price. This key-cost affiliation permits brief get admission to values based on their corresponding keys. Just like an actual-international dictionary, where phrases (keys) are related to their definitions (values), a dictionary data shape allows you to appearance up values with the aid of their associated keys.
The gain of using a dictionary is that it affords rapid retrieval and green searching of facts, as it makes use of a hashing or indexing mechanism internally. This makes dictionaries suitable for eventualities wherein you need to quickly get admission to or replace values based on their unique identifiers.
Therefore, whilst you want to associate items collectively and retrieve them using their corresponding keys, a dictionary is the right facts structure to apply.
Read more about dictionary at:
https://brainly.com/question/17197962
what are the two frames used in active scanning? (choose two)
Answers
During active scanning, a wireless client initiates the scanning process by sending Probe Request frames, and APs respond with Probe Response frames containing information about their respective networks. This allows the client to discover and assess available wireless networks before establishing a connection.
The two frames used in active scanning are:
Probe Request frame: A Probe Request frame is sent by a wireless client to discover available wireless networks in the vicinity. It is broadcasted to all nearby access points (APs) and contains information such as the client's capabilities and supported network protocols. The Probe Request frame prompts APs to respond with a Probe Response frame.
Probe Response frame: A Probe Response frame is sent by an AP in response to a Probe Request frame. It provides information about the AP, including its SSID (Service Set Identifier), supported data rates, security settings, and other relevant details. The Probe Response frame helps the client evaluate and select an appropriate AP to associate with.
Learn more about Probe Request here:
https://brainly.com/question/31936882
#SPJ11
17. Electrospinning is a broadly used technology for electrostatic fiber formation which utilizes electrical forces to produce polymer fibers with diameters ranging from 2 nm to several micrometers using polymer solutions of both natural and synthetic polymers. Write down 5 different factors that affect the fibers in this fabrication technique. (5p) 18. Write down the definition of a hydrogel and list 4 different biological function of it. (Sp) 19. A 2.0-m-long steel rod has a cross-sectional area of 0.30cm³. The rod is a part of a vertical support that holds a heavy 550-kg platform that hangs attached to the rod's lower end. Ignoring the weight of the rod, what is the tensile stress in the rod and the elongation of the rod under the stress? (Young's modulus for steel is 2.0×10"Pa). (15p)
Answers
The elongation of the rod under stress is 0.09 m or 9 cm. Five factors that affect the fibers in electrospinning fabrication technique.
1. Solution properties: The solution concentration, viscosity, surface tension, and conductivity are examples of solution properties that influence fiber morphology.
2. Parameters of electrospinning: Voltage, flow rate, distance from the needle to the collector, and needle gauge are examples of parameters that influence the fiber diameter and morphology.
3. Physicochemical properties of the polymer: The intrinsic properties of the polymer chain, such as molecular weight, crystallinity, and orientation, influence the morphology and properties of the fibers.
4. Ambient conditions: Humidity, temperature, and air flow rate can all influence fiber morphology.
5. Post-treatment: Electrospun fibers can be subjected to post-treatments such as annealing, solvent treatment, and crosslinking, which can influence their mechanical, physical, and chemical properties.Answer to question 18:A hydrogel is a soft, jelly-like material that is primarily composed of water and a polymer network. Hydrogels have a range of biological functions due to their properties such as mechanical and biocompatible. Some of the biological functions of hydrogel are mentioned below:
1. Drug delivery: Hydrogels are widely utilized in drug delivery systems, particularly for the sustained release of drugs over time.
2. Tissue engineering: Hydrogels are frequently used as biomaterials in tissue engineering due to their similarities to the extracellular matrix (ECM).
3. Wound healing: Hydrogels are employed in wound healing due to their potential to promote tissue regeneration and repair.
4. Biosensing: Hydrogels are utilized in the production of biosensors that are capable of detecting biological and chemical compounds. Answer to question 19:Given,Magnitude of the force acting on the rod, F = 550 kg × 9.8 m/s² = 5390 NArea of the cross-section of the rod, A = 0.30 cm³ = 0.3 × 10^-6 m³Length of the rod, L = 2.0 mYoung's modulus of steel, Y = 2.0 × 10¹¹ N/m²The tensile stress in the rod is given by the relation;Stress = Force / Areaσ = F / Aσ = 5390 N / 0.3 × 10^-6 m²σ = 1.80 × 10^10 N/m²The elongation of the rod under stress is given by the relation;Strain = Stress / Young's modulusε = σ / Yε = 1.80 × 10¹⁰ N/m² / 2.0 × 10¹¹ N/m²ε = 0.09. The elongation of the rod under stress is 0.09 m or 9 cm.
Learn more about morphology :
https://brainly.com/question/1378929
#SPJ11
which of the following is not linked with either expansionary or contractionary monetary policies?
A. Interest rates
B. Long run aggregate supply curve
C. Inflation rates
Answers
B. Long-run aggregate supply curve is not directly linked with either expansionary or contractionary monetary policies.
However, it can be indirectly impacted by these policies through their effects on overall economic growth and inflation. Both expansionary and contractionary monetary policies can have an impact on interest rates and inflation rates. Expansionary refers to a type of economic policy that aims to stimulate economic growth and increase aggregate demand in an economy. This is typically achieved through a combination of monetary and fiscal policies, such as lowering interest rates, increasing government spending, and cutting taxes. Expansionary policies are often implemented during times of economic downturns, such as recessions or depressions, in order to boost economic activity, create jobs, and promote investments. However, expansionary policies can also lead to inflation and other economic imbalances if not carefully managed. The effectiveness of expansionary policies can depend on a variety of factors, such as the state of the economy, the level of government intervention, and the degree of coordination between different policy measures.
Learn more about Expansionary here:
https://brainly.com/question/28274222
#SPJ11
Discuss the use of spreadsheet software compared to database software to store and manipulate student data.
Answers
Explanation:
Because databases store information more efficiently, databases can handle volumes of information that would be unmanageable in a spreadsheet. Spreadsheets have record limitations whereas databases do not. Compared to databases, spreadsheets can require a large amount of hard-drive space for data storage.
Do you believe that Online Activism results in real change, or do you think it is something that people do to make themselves look good/feel better about themselves? Look for some examples of both in recent history to back your point.
Reflect your findings in a 350 word discussion post. Be sure to link to multiple online sources and add in visual and other multimedia resources to help you make your point. Be sure you credit your sources via a linkback. You are considering other’s ideas, so they need to be credited as such.
Answers
Online Activism results in relatively minimal change. The reason behind this matter is because people generally only take action virtually and not in real life. Although there are fewer opportunities to take action in person, there is a relatively strong difference of seeing someone dying of cancer online and seeing someone in person dying of cancer. This can be summed down to sympathetic disconnect, being how virtualization creates a disconnect between people emotionally and causes the static statement of, "There's nothing I can do" when there's donations and organizations to contribute to always there. It's much easier to feel included in person than online, and accordingly, much more often a reason for people to interact and take actual action.
Select the correct navigational path to hide a worksheet.
Click the ____ tab on the ribbon to the Cells gallery.
Select ___ and use that drop-down menu to select ____.
Then Hide sheet.
Answers
Answer:
Home, Format, Hide & Unhide.
Explanation:
A person with a low number of white blood cells could have difficulty in fighting infections and A decrease in the number of lymphoid stem cells could result in a decrease in red blood cell.
What is nucleotide?It is the sub units and buIlding blocks of DNA. It is made up of a five-sided sugar, phosphate group and then a nitrogen base.
These groups make the backbone of the DNA helix. If you look at a DNA helix, they make the side of the ladder or the side portion. They connect to a nitrogen base which make the steps of the ladder. The type of sugar that is used in a DNA helix is called deoxyribose.
Nitrogen bases are the molecules that make up the steps of the ladders. There are four different nitrogen bases, namely; Guanine, Thymine,Adenine and Cytosine.
Pyrimidines are compounds that make a single 6-sided ring. Examples of pyrimidines are Cytosine and Thymine. Purines on the other hand make 5-sided and 6-sided rings.
Therefore, A person with a low number of white blood cells could have difficulty in fighting infections and A decrease in the number of lymphoid stem cells could result in a decrease in red blood cell.
Learn more about white blood cells on:
https://brainly.com/question/19202269
#SPJ5
what elements of the user stories were the most helpful in developing your initial test cases?
Answers
The most helpful elements of user stories in developing initial test cases are: the clear description of the user's goal, the defined roles and actions, and the specific acceptance criteria.
When developing test cases from user stories, it is important to consider the following elements:
1. User persona: User personas provide a better understanding of the user's needs, goals, and behavior. This information is used to develop relevant test cases.
2. User story title: The title of the user story is used to create a test case name.
3. Acceptance criteria: Acceptance criteria provide details on the expected outcome or behavior of the application.
4. Assumptions: Assumptions provide insight into the expected user behavior and are helpful in developing test cases.
5. Business value: Business value helps to prioritize which test cases should be executed first.
Learn more about developing initial test: https://brainly.com/question/14923867
#SPJ11
/* Given an array of ints, return true if the array contains a 2 next to * a 2 or a 4 next to a 4, but not both.
*/
public boolean either24(int[] nums) {
boolean has22 = false;
boolean has44 = false;
for(int i = 0; i < nums.length - 1; i++) {
if(nums[i] == 2 && nums[i+1] == 2)
has22 = true;
if(nums[i] == 4 && nums[i+1] == 4)
has44 = true;
}
return has22 != has44;
}
Answers
The given algorithm checks if an array contains either a pair of adjacent 2's or a pair of adjacent 4's, but not both. Here's how it works:
Initialize two boolean variables, has22 and has44, to keep track of whether a pair of adjacent 2's and 4's are found, respectively. Set both variables to false initially.
Iterate through the array from the first element to the second-to-last element (i = 0 to nums.length - 2).
For each element at index i:
If nums[i] is 2 and nums[i+1] is also 2, set has22 to true.
If nums[i] is 4 and nums[i+1] is also 4, set has44 to true.
After iterating through the array, check if has22 is not equal to has44 using the != operator.
If has22 is true and has44 is false (or vice versa), return true.
If both has22 and has44 are true, or both are false, return false.
The return value indicates whether the array contains either a pair of adjacent 2's or a pair of adjacent 4's, but not both.
By examining each adjacent pair of elements, the algorithm determines the presence of specific pairs and ensures that only one type of pair is found in the array.
To learn more about array click on the link below:
brainly.com/question/30489113
#SPJ11
consider the er diagram in figure 3.24. assume that a course may or may not use a textbook, but that a text by definition is a book that is used in some course. a course may not use more than five books. instructors teach from two to four courses. supply (min, max) constraints on this diagram. state clearly any additional assumptions you make. if we add the relationship adopts, to indicate the textbook(s) that an instructor uses for a course, should it be a binary relationship between instructor and text, or a ternary relationship among all three entity types? what (min, max) constraints would you put on the relationship? why?
Answers
The (min, max) constraints depicted in Figure B will be present in the final ER Diagram.
What is entity relationship model give an example?Real-world objects are represented by an ER model. In the real world, an entity is a thing or object that stands out from the surrounding environment. An organization's employees, for instance, are distinct entities.
Taking into account the additional following assumptions: - Only one instructor teaches each course. - Only one course makes use of each textbook. - The use of a textbook by an instructor is not required for all courses. If there is a text: - ___ It is utilized in a specific course, so the instructor who teaches that course adopts it. When a text is used in a course taught by an instructor, it is considered adopted.
The constraints (min., max.) depicted in Figure B will be present in the final ER Diagram.
To learn more about ER visit :
https://brainly.com/question/30873853
#SPJ1
(ANYONE GOOD AT PYTHON!?)
Write a program that outputs some Leaderboard. Pick something that interests you.
You must have a minimum of 3 rows of data and 2 columns (name can be one).
I created 6 variables called player_1, player_2 and player_3, points_1, points_2 and points_3. Be sure to use meaningful names. I centered the names and right-justified the total points. You may format your data to your liking, but the output must be in clean rows and columns.
Answers
Answer:
# Python Recap
def main():
runTimeInMinutes = 95
movieTitle = "Daddy Day Care"
print(movieTitle)
movieTitle = "Hotel for Dogs"
print(movieTitle)
print(runTimeInMinutes)
main()
Explanation:
SOMEONE PLEASE HELP ME OUT !!!!!!

Answers
Answer:
not completly sure but i believe its the one that says inform the coach of where the goalies weak area...
Explanation:
how is static filtering different from dynamic filtering of packets? which is perceived to offer improved security?
Answers
The dynamic packet filtering firewall only permits a specific packet with a specific source, destination, and port address to pass through the firewall.
The dynamic packet filtering firewall only permits a specific packet with a specific source, destination, and port address to pass through the firewall. Static filtering firewalls permit entire sets of one type of packet to enter in response to authorized requests.
Stateful inspection, often referred to as dynamic packet filtering, is a firewall technology that keeps track of the status of active connections and makes decisions about which network packets to let pass through the firewall based on this data.
A static filter is one that has a predefined value that cannot be modified once it has been applied. For each viewer, the data is always filtered in the same way.
To know more about dynamic packet click here:
https://brainly.com/question/13567404
#SPJ4
Spreadsheet allow three types of cell addressing. They include ______addresses, such as $E$1, ______addresses, such as R$3, and ______addresses, such as D4.
Answers
Answer:
The answer is below
Explanation:
Based on the Microsoft Excel Formatting style, Spreadsheet allows three types of cell addressing. They include:
1. ABSOLUTE CELL ADDRESSING addresses, such as $E$1,
2. MIXED CELL ADDRESSING addresses, such as R$3, and
3. RELATIVE CELL ADDRESSING addresses, such as D4.
Does anyone know the answer for 4.2 Code Practice: Question 1 on edhesive
Answers
Answer:
Question 1
sum=0
count=0
while(sum<=100):
x=int(input("Enter a nmber"))
sum=sum+x
count=count+1
print("Sum: "+str(sum))
print("Numbers Entered: "+str(count))
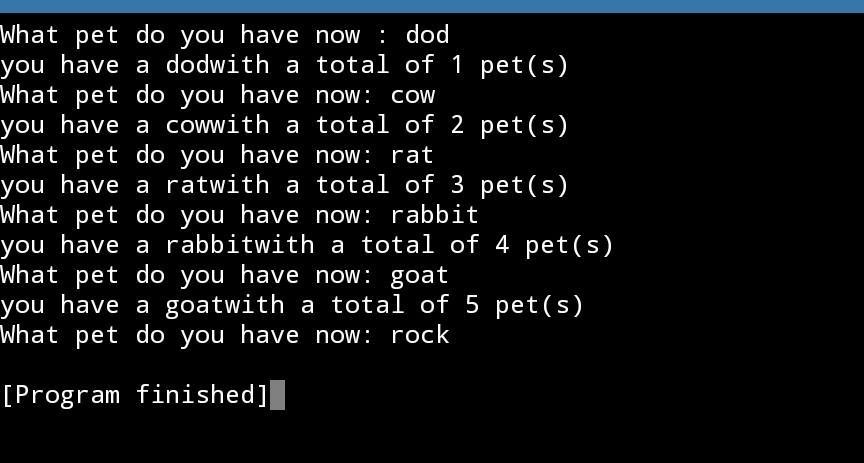
Question 2
count = 0
pet = (input("What pet do you have? "))
while(pet != "rock"):
count = count +1
print("You have a " + pet +" with a total of " + str(count) + " pet(s)")
pet = (input("What pet do you have? "))
Explanation:
The required program written in python 3 which continues to request user to input a pet name until a rock is entered is as follows :
pet = input('What pet do you have now : ')
#request an input from the user and store in the variable pet
total = 0
#initialize the total number of pets owned to 0
while (pet != 'rock'):
#while loop ensures that program runs until a rock is inputted by the user
total +=1
#adds one to the total after each loop
print('you have a ' + str(pet) + 'with a total of ' + str(total) + ' pet(s)')
#displays the formatted string using the total and pet variables which continues to update
pet = input('What pet do you have now: ')
#requests user to input pet name again as long as rock has not been supplied.
Therefore, an output of the program written is attached below.
Learn more on python programs :https://brainly.com/question/18685986
does anyone have a pdf of the greatest by eddie van der meer????
Answers
Answer
aight' so im finding it but i have to asnwer before someone else so look in the comments for it.
Explanation:
Just wait i getting it rn
import java.util.Scanner;
public class PigLatin {
public static void main(String args[]) {
Scanner console =new Scanner(System.in);
System.out.println("Please enter a word");
String phrase=console.nextLine();
System.out.println(eachWord(phrase));
}
public static String eachWord(String phrase) {
String help[]=phrase.split(" ");
for(int i=0; i
if (help[i].charAt(0) == 'a'){
return help[i] + "-ay";
}
if (help[i].charAt(0) == 'e'){
return help[i] + "-ay";
}
if (help[i].charAt(0) == 'i'){
return help[i] + "-ay";
}
if (help[i].charAt(0) == 'o'){
return help[i] + "-ay";
}
if (help[i].charAt(0) == 'u'){
return help[i] + "-ay";
}
if (help[i].charAt(0) == 'A'){
return help[i] + "-ay";
}
if (help[i].charAt(0) == 'E'){
return help[i] + "-ay";
}
if (help[i].charAt(0) == 'I'){
return help[i] + "-ay";
}
if (help[i].charAt(0) == 'O'){
return help[i] + "-ay";
}
if (help[i].charAt(0) == 'U'){
return help[i] + "-ay";
}
else {
return help[i].substring(1)+"-"+help[i].charAt(0)+"ay";
}
}
return "aoujbfgaiubsgasdfasd";
}
I need help with this Pig Latin Program. I want to split the string so each word can run through the method eachWord. I don't know how to revamp this!
Answers
Answer:b
Explanation:
I took quiz
Answer:
uuuuuuuuuuhhm
Explanation:
CODE!
Select the correct answer.
Which of the following is a scientific language used to create data science applications?
A. C
B. Java
C.FORTRAN
D. Swift
E. Python
I REALLY NEED HELP ASAP!!!!
Answers
The option of scientific language used to create data science applications is Python.
What is Python?Computer programming is known to be the act or process that people often use to write code that are meant to instructs how a computer, application or software program needs to run.
Note that Python is the most commonly used data science programming language. It is regarded as an open-source, very easy to learn and use language.
Learn more about Python from
https://brainly.com/question/12684788
Answer:
FORTRAN
Explanation:
Plato/edmentum
Your network has a network address of 172.17.0.0 with a subnet mask of 255.255.255.0.
Which of the following are true concerning this network? (Select two.)
answer choices
254 IP addresses can be assigned to host devices.
256 IP addresses can be assigned to host devices.
172.17.0.255 is the network broadcast address.
Answers
With a subnet mask of 255.255.255.0, your network's network address is 172.17.0.0. In addition, this network's 172.17.2.0 subnet is genuine, and there are 254 accessible host addresses.
What is subnet?A subnet, which is another name for a subnetwork, is a portion of a larger network that has been divided up. Subnets are the logical partition of an IP network into several smaller network segments, or subnets in more technical words.The protocol used to transport data from one computer to another via the internet is called the Internet Protocol (IP). A logical division of an IP network is called a subnetwork or subnet. Subnetting is the process of splitting an existing network into two or more separate networks. In their IP addresses, computers with the same subnet address use the same most-significant bit-group. A subnet is a subnetwork that belongs to a network and is in the class A, B, or C range. A class B network, for instance, is 172.16.0.0/16. Starting with 172.16, this network is quite large.To learn more about subnet, refer to:
https://brainly.com/question/29527004
This assignment is meant to give an alternative viewpoint to counting that is through the programming lens. 1. Consider the python code below: Numbers = [1, 2, 3, 4, 5, 6] Counter = 0 for i in Numbers: for j in Numbers: for k in Numbers: print (i, j, k) Counter = Counter + 1 print (Counter) (a) What is the above code counting? (b) Justify that the code is actually counting what you claim. (c) If Numbers has n entries, give a closed formula for the number of objects being counted. (a) Can you give a more efficient way to write the above code? If so, explain how it is counting the same objects as in (a).
Answers
The above code is counting all possible combinations of three numbers from the list Numbers.
(b) The code consists of three nested loops, each iterating over the elements of the list Numbers. The print statement inside the innermost loop outputs the current combination of three numbers. The counter variable keeps track of the total count of combinations. By incrementing the counter inside the innermost loop, we ensure that it counts every valid combination.
(c) If Numbers has n entries, the number of objects being counted can be determined by calculating the number of permutations of three elements from n. This can be calculated using the formula:
Number of objects = nP3 = n! / (n-3)!
(a) A more efficient way to write the code is by using the itertools module in Python, specifically the combinations() function. This function generates all possible combinations of a given length from an iterable. Here's an example of how the code can be rewritten using combinations():
Numbers = [1, 2, 3, 4, 5, 6]
Counter = 0
for combination in itertools.combinations(Numbers, 3):
print(combination)
Counter += 1
print(Counter)
In this code, itertools.combinations() generates all combinations of length 3 from the Numbers list. Each combination is directly printed, and the counter is incremented accordingly. This code counts the same objects as the previous implementation, which is all possible combinations of three numbers from the given list. However, using itertools.combinations() provides a more concise and efficient approach.
Know more about permutations here:
https://brainly.com/question/29990226
#SPJ11
1. what is the internet infrastructure stack? what is the relevance of this technological concept to marketers? what is the significance of cloud computing in relationship to the internet infrastructure? who is the leader in cloud computing for third parties by revenue, cisco, ibm, , or amazon?
Answers
The correct answer is Internet infrastructure stack are sets of hardware and services combined together which helps in making the data and information available on the web page.
Any hardware component that is housed inside a computer. a set of guidelines or software that instructs a computer on what to do or how to carry out a certain task (computer software runs on hardware). a computer application that gives users the resources they need to do a certain task. any hardware component that is housed inside a computer. a set of guidelines or software that instructs a computer on what to do or how to carry out a certain task (computer software runs on hardware). a computer application that gives users the resources they need to do a certain task.
To learn more about hardware click on the link below:
brainly.com/question/15232088
#SPJ4
Which phrase best describes a countrys monetray base?
A. Only money that cannot be easily spent
B. Only currency and coins in circulation in the economy
C. All money invested in the stock market
D. All money in circulation throughout the economy
(Economics and Finance)
Please be quick I'm doing Apex