Lab 6B: printing a binary number
This lab asks you to use string formatting to print a binary number. First you will prompt the user for an integer, using exactly the prompt "Enter a decimal integer: " including the colon character and a space following it. Then print out the decimal number and it's binary equivalent. You do not need to do any mathematical conversion of the integer to binary, you can use the format method.
For example, if the prompt and input are
Enter a decimal integer: 10
The output would be
10 in binary is 1010
If the prompt and input are
Enter a decimal integer: 367
The output would be
367 in binary is 101101111
Answers
Answer:
In Python:
num = int(input("Enter a decimal integer: "))
temp = num
bin = ""
while num > 0:
bin = str(num%2)+bin
num//=2
print(str(temp)+" in binary is "+str(bin))
Explanation:
This prompts the user for a decimal number
num = int(input("Enter a decimal integer: "))
This assigns the input number to a temporary variable
temp = num
This initializes the binary output to an empty string
bin = ""
This loop is repeated while num is greater than 0
while num > 0:
This appends the remainder of num divided by 2 to the front of the binary variable bin
bin = str(num%2)+bin
This calculates the floor division of num and 2
num//=2
This prints the required output
print(str(temp)+" in binary is "+str(bin))
Related Questions
Across the breadth of decision domains,
O The greater use of intuition over analytics results in stronger organizational
performance
The greater use of analytics over intuition results in stronger organizational
performance
O The use of analytics over intuition results in improved performance in about 75 percent
of the decision domains
O The use of analytics over intuition results in improved performance in about 50 percent
of the decision domains
Answers
Answer: C. The use of analytics over intuition results in improved performance in about 50 percent of decision domains.
Explanation: This suggests that while analytics can be a powerful tool for decision-making, there are still many situations in which intuition plays an important role. It is important for organizations to strike a balance between using analytics and intuition to make decisions that lead to improved performance.
taxpayers with home offices who use the actual expense method for computing home office expenses must allocate indirect expenses of the home between personal use and home office use. only expenses allocated to the home office use are deductible. group starts
Answers
Taxpayers who utilize the actual expense technique to calculate their home office expenses must divide their home's indirect costs between personal and business use. Only costs related to using a home office are deductable. which is accurate, the group begins.
Are home office expenses direct or indirect?Direct business expenses are entirely deductible. The portion of your home's square footage that is exclusively used for your business is the amount of indirect home office expenses that are partially deductible.
Regular Method: You divide the costs of maintaining the home between your personal and business use to determine the deduction for home office expenses. You are allowed to deduct all of your direct business expenses, and you are allowed to divide your home's total indirect costs according to the amount of its floor space that is used for your business.
The permitted square footage is multiplied by the recommended rate to get the amount of deductible expenses.The lesser of 300 square feet or the portion of a home used for a permissible business use is the permitted square footage.The recommended price is $5.
To learn more about office expense refer to :
https://brainly.com/question/25811981
#SPJ4
You just started your new position at a small doctor’s office. A nurse asks you to print out a report for a patient. The patient’s name is Tim Drake, but you find multiple files with that name. You discover that the files are named differently. Looking at the files for Mr. Drake, you find the following files:
01_DrakeTim
DrakeTim_A
TimDrake001
timdrake
2. Initial Post: Create a new thread and answer all three parts of the initial prompt below
What methods could you use to help you find the files you need?
Why is choosing a descriptive or detailed name for your files a useful practice?
What recommendations might you make to the office manager to better organize the office files?
Answers
To find the files for Tim Drake, who has multiple files with different naming conventions, you can use the following methods:
Search Function: Utilize the search function in the file management system or operating system. Enter the name "Tim Drake" or a variation of it to locate the relevant files. The search function will scan file names and contents, making it easier to find the specific files you need.
Sorting: Sort the files by name, date modified, or any other relevant criteria. This can help group similar files together and make it easier to identify the correct ones. For example, sorting the files alphabetically will cluster the files with similar names closer to each other.
File Metadata: Check the metadata or properties of the files. Some file systems allow you to add tags or keywords to files, making it easier to search for them based on specific attributes. Ensure that the files are properly tagged with relevant information like patient names, dates, or other identifying details.
Choosing descriptive or detailed names for files is a useful practice for several reasons:
Easy Identification: A descriptive file name provides clear information about the content or purpose of the file. When you or others need to locate a specific file, a well-named file can be easily identified among many others. It reduces confusion and saves time.
Organization: Descriptive file names help in organizing files within a system. By using meaningful names, files can be grouped or sorted based on their purpose, type, or relevance. This enhances overall file management and facilitates efficient retrieval of information.
Clarity and Consistency: A consistent naming convention ensures uniformity and clarity across files. It helps maintain a standardized structure and allows for easy understanding of file names by all users. This consistency improves collaboration and reduces errors.
To better organize the office files, the following recommendations can be made to the office manager:
Implement a File Naming Convention: Establish a standardized naming convention for files that includes relevant details such as patient names, dates, and file types. Ensure that all staff members adhere to this convention when creating or saving files. This will promote consistency and ease of file retrieval.
Folder Structure: Create a well-structured folder hierarchy based on categories, such as patient names, departments, or file types. This arrangement should be intuitive and reflect the needs of the office. Maintain consistency throughout the folder structure to facilitate easy navigation and organization of files.
Document Management System: Consider implementing a document management system (DMS) or electronic health record (EHR) system to centralize and streamline file management. These systems offer features like robust search capabilities, metadata tagging, version control, and secure access controls. They can greatly improve file organization and retrieval efficiency.
For more questions on conventions
https://brainly.com/question/31174724
#SPJ11
Given integer currentBananas, if the number of bananas is 5 or more but fewer than or equal to 20, output "Allowable batch", followed by a newline.
Ex: If the input is 18, then the output is:
Allowable batch
Answers
To implement this in C++, you can use an if statement to check if the value of currentBananas is within the given range.
How to implement the statement in c++?A sample code for implementing the check for the allowable batch of currentbananas would be:
#include <iostream>
int main() {
int currentBananas;
std::cin >> currentBananas;
if (currentBananas >= 5 && currentBananas <= 20) {
std::cout << "Allowable batch" << std::endl;
}
return 0;
}
This code takes an integer input for currentBananas and checks if its value is greater than or equal to 5 and less than or equal to 20. If the condition is true, it prints "Allowable batch" followed by a newline.
Find out more on input at https://brainly.com/question/13885665
#SPJ1
Explain the concept of Informed Consent?
Answers
Which of the following statements about mentors is true?
A. Most companies do not support mentoring programs.
B. Mentors rarely provide real-life and practical advice.
C. Mentors are an excellent way to learn on the job.
D. Leaders in high positions rarely have time to be mentors.
Answers
Among the given options, statement C is true. Mentors play a crucial role in providing guidance, support, and practical advice to individuals seeking to learn and grow in their professional lives. Mentoring programs are commonly supported by companies as they recognize the value of mentorship in developing talent, enhancing skills, and fostering career advancement. Mentors bring their experience and expertise to the table, sharing real-life insights and offering guidance based on their own professional journey. They provide valuable knowledge, wisdom, and support, making them an excellent resource for learning and development.
A message with 3000 bytes gets encoded using the scheme Base64. What will be the size of the encoded message?
Answers
Answer:
4000 characters
Explanation:
Base64 encodes each set of three bytes into four bytes.
So 3000 * 4/3 = 4000 characters.
A company has a number of employees. The attributes of EMPLOYEE include Employee ID (identifier), Name, Address, and Birthdate. The company also has several projects. Attributes of PROJECT include Project ID (identifier), Project Name, and Start Date. Each employee may be assigned to one or more projects or may not be assigned to a project. A project must have at least one employee assigned and may have any number of employees assigned. An employee’s billing rate may vary by project, and thecompany wishes to record the applicable billing rate (billing Rate) for each employee when assigned to a particular project.
Required:
Draw an ERD for this company.
Answers
Answer:
The ERD is attached.
Explanation:
See the attached document for ERD
Which of the following BEST describes what a kilobyte is a measurement of?
CPU speed
Power level
Back
Data throughput
Storage space
Answers
Answer:
Storage space
Explanation:
WHICH OF THESE COMMANDS ALLOWS YOU TO NAVIGATE TO THE OUTLINE FILE THAT WILL BE INTEGRATED INTO A PRESENTATION?
Answers
The question seems to be asking about commands that allow you to navigate to an outline file for integration into a presentation.
How to go about this?However, without specific information about the software or tools being used, it is difficult to provide a specific command.
Generally, in presentation software like Microsoft PowerPoint, you can navigate to an outline file by going to the "File" menu, selecting "Open," and choosing the appropriate file.
Other presentation tools may have similar options to navigate to and open an outline file.
Learn more about command at:
https://brainly.com/question/25808182
#SPJ1
An operator is a symbol that tells the computer?
Answers
Answer:
An operator in a programming language is a symbol that tells the compiler or interpreter to perform specific mathematical, relational or logical operation and produce final result.
The difference between Return key and word Wrap
Answers
List and briefly describe various types of Malware?
Answers
Answer:
Here yah go.
Explanation:
Virus: A virus is a malicious program that attaches itself to legitimate files and spreads by infecting other files. It can cause damage to the infected system by corrupting or deleting files, slowing down the computer, or spreading to other connected devices.
Worm: Worms are self-replicating programs that spread over computer networks without the need for user interaction. They exploit vulnerabilities in operating systems or software to propagate themselves and can cause significant damage by consuming network bandwidth or carrying out malicious activities.
Trojan Horse: A Trojan horse appears as a legitimate and harmless program, but it contains malicious code that performs unauthorized activities without the user's knowledge. Trojans can enable remote access to a computer, steal sensitive information, or download and install additional malware.
Ransomware: Ransomware is a type of malware that encrypts a victim's files, making them inaccessible until a ransom is paid. It typically displays a ransom note, demanding payment in exchange for the decryption key. Ransomware attacks can be highly disruptive and costly for individuals and organizations.
Spyware: Spyware is designed to secretly monitor a user's activities and gather information without their consent. It can track keystrokes, capture screenshots, record browsing habits, and steal personal or sensitive data. Spyware often aims to collect financial information or login credentials.
Adware: Adware is a type of malware that displays unwanted advertisements on a user's computer. It can redirect web browsers, modify search results, and slow down system performance. Adware is typically bundled with legitimate software and generates revenue for its creators through advertising clicks or impressions.
Keylogger: Keyloggers are designed to record keystrokes on a computer or mobile device. They can capture usernames, passwords, credit card details, and other confidential information. Keyloggers can be delivered through malicious downloads, infected websites, or email attachments.
Botnet: A botnet is a network of compromised computers, also known as "zombies" or "bots," that are controlled by a central command and control (C&C) server. Botnets can be used for various malicious activities, including distributed denial-of-service (DDoS) attacks, spam distribution, or spreading other types of malware.
Rootkit: A rootkit is a type of malware that provides unauthorized access and control over a computer system while hiding its presence from detection by security software. Rootkits often modify operating system components and can be difficult to detect and remove.
Backdoor: A backdoor is a hidden entry point in a system that bypasses normal authentication mechanisms, allowing unauthorized access to a computer or network. Backdoors are often used by attackers to gain persistent access for further exploitation or to create a secret pathway for future access.
It is essential to stay vigilant, use reputable antivirus software, keep systems up to date, and exercise caution when downloading files or clicking on suspicious links to protect against these various types of malware.
what are the advantages of using a vpn?
Answers
Answer:
Changing ip address to avoid ip ban. keeping your personal info safe while on public connections
Explanation:
Looked it up.
Write a program that reads a file called 'test.txt' and prints out the contents on the screen after removing all spaces and newlines. Punctuations will be preserved. For example, if 'test.txt' contains: This is a test file, for chapter 06. This a new line in the file! Then, your program's output will show: Thisisatestfile,forchapter06.Thisanewlineinthefile! Hint: Consider using the 'strip()' and 'replace()' functions.
Answers
Answer:
I don't know you should figure that out good luck
Explanation:
good luck
QUESTION NO-1: The Highest quality printer is dot-matrix True False Prev
Answers
It is false that the Highest quality printer is basically dot-matrix.
What is dot-matrix?A dot matrix is a patterned 2-dimensional array used to represent characters, symbols, and images.
Dot matrices are used to display information in most types of modern technology, including mobile phones, televisions, and printers. The system is also used in the textile industry for sewing, knitting, and weaving.
Dot-matrix printers are an older technology that uses pins to strike an ink ribbon in order to print characters and images on paper.
While dot-matrix printers are capable of producing multi-part forms and have low operating costs, they are generally regarded as having lower print quality when compared to more modern printer technologies.
Thus, the given statement is false.
For more details regarding dot-matrix, visit:
https://brainly.com/question/4953466
#SPJ9
what is the entity relationship model?
Answers
You and your roommate decide to reduce your environmental impact by recycling more, going paperless, and using environmentally safe cleaning products. You know you also can use green computing tactics to reduce electronic waste, minimize power use, and more. Create a list of five reasons why you should add green computing to your efforts. List 10 ways you can apply green computing to your daily life.
Answers
Answer:
first one is (a) next one is (b)
Explanation:
By integrating the following green computing practices into your daily life, you and your roommate can make a meaningful contribution to environmental conservation and sustainability.
Five Reasons to Add Green Computing to Your Efforts:Reduce Electronic Waste: Green computing involves extending the lifespan of electronic devices through efficient usage and proper disposal. By adopting green computing practices, you can contribute to the reduction of electronic waste, which is a significant environmental concern.
Minimize Energy Consumption: Green computing focuses on using electronic devices more efficiently to reduce energy consumption. This not only saves you money on energy bills but also helps lower overall energy demand, leading to a decrease in greenhouse gas emissions.
Extend Device Lifespan: By practicing responsible usage, such as shutting down or putting devices in low-power modes when not in use, you can extend the lifespan of your electronics. This reduces the need for frequent replacements, saving resources and energy.
Promote Sustainable Manufacturing: The demand for new electronic devices contributes to resource extraction and energy-intensive manufacturing processes. Green computing practices encourage people to make more conscious purchasing decisions, supporting sustainable manufacturing practices.
Contribute to a Greener Future: Embracing green computing aligns with broader environmental goals and initiatives. By incorporating these practices into your daily life, you become part of a collective effort to create a more sustainable and eco-friendly future.
Ways to Apply Green Computing to Your Daily Life:
Power Management: Enable power-saving features on your devices, such as sleep mode and automatic screen dimming, to reduce energy consumption when idle.
Unplug Chargers: Unplug chargers and power cords when not in use, as they continue to draw energy even when devices are not connected.
Energy-Efficient Devices: When purchasing new devices, opt for those with Energy Star certifications or energy-efficient ratings to reduce overall energy consumption.
Digital Documentation: Transition to digital documentation and e-receipts to reduce paper usage and the need for physical storage.
Cloud Storage: Utilize cloud storage for data and files, which reduces the need for physical storage devices and their associated energy consumption.
Eco-Friendly Cleaning: Use eco-friendly cleaning products to clean your devices and workspaces, avoiding harmful chemicals that can impact both your health and the environment.
Virtual Meetings: Opt for virtual meetings and communication tools to reduce the need for travel and associated carbon emissions.
Server Consolidation: If you run servers for personal use or small projects, consider consolidating them to use fewer resources and minimize power consumption.
Learn more about environmental conservation click;
https://brainly.com/question/27439044
#SPJ3
3
Drag each label to the correct location on the image.
An organization has decided to initiate a business project. The project management team needs to prepare the project proposal and business
justification documents. Help the management team match the purpose and content of the documents.
contains high-level details
of the proposed project
contains a preliminary timeline
of the project
helps to determine the project type,
scope, time, cost, and classification
helps to determine whether the
project needs meets business
needs
contains cost estimates,
project requirements, and risks
helps to determine the stakeholders
relevant to the project
Project proposal
Business justification
Answers
Here's the correct match for the purpose and content of the documents:
The Correct Matching of the documentsProject proposal: contains high-level details of the proposed project, contains a preliminary timeline of the project, helps to determine the project type, scope, time, cost, and classification, helps to determine the stakeholders relevant to the project.
Business justification: helps to determine whether the project needs meet business needs, contains cost estimates, project requirements, and risks.
Please note that the purpose and content of these documents may vary depending on the organization and specific project. However, this is a general guideline for matching the labels to the documents.
Read more about Project proposal here:
https://brainly.com/question/29307495
#SPJ1
A company wants to automatically adjust its IT resources to meet changing demand and minimize costs as it expands its operations. Which feature is most important for the company to achieve this goal rapidly
Answers
The most important feature for the company to achieve rapid adjustment of IT resources and minimize costs as it expands its operations is an elastic and scalable infrastructure.
An elastic infrastructure allows the company to dynamically allocate and deallocate IT resources based on demand fluctuations. This ensures that the company can scale its resources up or down quickly and efficiently in response to changing needs.
By utilizing an elastic infrastructure, the company can automatically adjust its IT resources to meet increased demand during peak periods and scale them down during periods of low demand. This flexibility enables the company to optimize resource allocation and minimize costs, as it only pays for the resources it actually needs at any given time.
In order to implement an elastic infrastructure, the company should consider adopting cloud computing technologies, such as Infrastructure as a Service (IaaS) or Platform as a Service (PaaS) solutions. Cloud providers offer scalable resources that can be provisioned and deprovisioned on-demand, allowing the company to rapidly adjust its infrastructure to match demand.
Additionally, implementing automated monitoring and resource management systems can help the company track usage patterns, detect changes in demand, and trigger automatic adjustments to IT resources. This level of automation ensures a rapid response to changing demand, enabling the company to effectively optimize its IT resources while minimizing costs.
For more such questions on infrastructure
https://brainly.com/question/14237202
#SPJ11
find HTML CODE FOR THIS

Answers
The HTML code for the above is given as follows
<table>
<tr>
<th>Country</th>
<th>Year</th>
<th>Population (In Crores)</th>
</tr>
<tr>
<td rowspan="3">India</td>
<td>1998</td>
<td>85</td>
</tr>
<tr>
<td>1999</td>
<td>90</td>
</tr>
<tr>
<td>2000</td>
<td>100</td>
</tr>
<tr>
<td rowspan="3">USA</td>
<td>1998</td>
<td>30</td>
</tr>
<tr>
<td>1999</td>
<td>35</td>
</tr>
<tr>
<td>2000</td>
<td>40</td>
</tr>
<tr>
<td rowspan="3">UK</td>
<td>1998</td>
<td>25</td>
</tr>
<tr>
<td>1999</td>
<td>30</td>
</tr>
<tr>
<td>2000</td>
<td>35</td>
</tr>
</table>
Why are HTML Codes Important?HTML codes are important because theydefine the structure and content of webpages.
They provide a standardized way to format and present information, including text,images, links, and multimedia.
HTML codes allow web browsers to interpretand render web content, enabling users to access and navigate websites effectively.
Learn more about HTML Codes:
https://brainly.com/question/4056554
#SPJ1
addGrocery public void addGrocery (Grocery groc) Adds the given Grocery parameter to the grocList. Parameters: groc - Grocery object to be added to the ArrayList removeGrocery public void removeGrocery (String grocName) Loops through the grocList until the given grocName is found then it is removed from the list. Grocery.getName() will prove useful. Parameters: grocName - Name of Grocery object to remove. toString public String toString() Loops through the grocList ArrayList and appends the toString() of each Grocery object to the strList variable. Using the Grocery.toString() method from the Grocery class will be handy for this method. Each entry will have newline character between them. '\n' Broccoli which costs: $2.99, located in the aisle 12. Cheese which costs: $1.50, located in the aisle 3. Rop Tamen which costs: $4.25, located in the aisle 14. Overrides: toString in class Object getAisleGroceries public String getAisleGroceries (int aisle) Loops through the grocList and checks each Grocery object's aisle against the aisle parameter provided. Each Grocery that has the same aisle has its Grocery.toString() added to the aisleString variable, along with a newline character, '\n'. Grocery.getAisle () will come in handy. Parameters: aisle - Int indicating which aisle groceries are being looked for. 1 2 3 4 5 6 7 8 9 10 11 12 13 14 فر فر 12 456 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 import java.util.ArrayList; public class GroceryList { ArrayList grocList = new ArrayList(); public ArrayList getGrocList() { return grocList; } public void addGrocery (Grocery groc) { grocList.add(groc); } /* * Student Self-Explanation: * * * */ public void removeGrocery (String grocName) { for (Grocery g: grocList) { if(false) { //TODO Student grocList.remove(g); break; } public String toString() { String strList = ""; //TODO Student return strList; } public String getAisleGroceries (int aisle) { String aisleString = ""; //TODO Student return aisleString; } public String getTotals() { double priceSum = 0; int calories Sum = 0; for (Grocery g: grocList) { priceSum + g.getPrice();
Answers
In coding and programming, an array is a collection of items, or data, stored in contiguous memory locations, also known as database systems .
What is an array and example?An array is a collection of similar types of data. For example, if we want to store the names of 100 people then we can create an array of the string type that can store 100 names. String[] array = new String[100]; Here, the above array cannot store more than 100 names.An array is a linear data structure that collects elements of the same data type and stores them in contiguous and adjacent memory locations. Arrays work on an index system starting from 0 to (n-1), where n is the size of the array.Array in C can be defined as a method of clubbing multiple entities of similar type into a larger group. These entities or elements can be of int, float, char, or double data type or can be of user-defined data types too like structures.Arrays are used to implement data structures like a stack, queue, etc. Arrays are used for matrices and other mathematical implementations. Arrays are used in lookup tables in computers. Arrays can be used for CPU scheduling.There are two types of arrays:
One-Dimensional Arrays.Multi-Dimensional Arrays.//importing package java.util.ArrayList to use ArrayList in the program
import java.util.ArrayList;
import java.util.Date;
public class test_array_list {
// Main method
public static void main(String[] args) {
// Create an array list of objects
ArrayList<Object> s = new ArrayList<Object>();
s.add(new Loan());
s.add(new Date());
s.add(new String("String class"));
s.add(new Circle());
// Display all the elements in the list by
// invoking the object’s to String() method
for (int element = 0; element < o.size(); element++) {
System.out.println((s.get(element)).toString());
}
}
}
To learn more about Array refer to:
https://brainly.com/question/28061186
#SPJ4
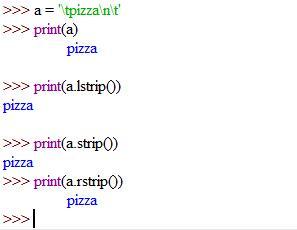
#Question 4: #Use a variable to represent the name of a food. You are then going to print this variable four times. Before you do, Print the food out and include some white space characters at the beginning and end and use "\t" and "\n" a least once. Then print the food once so the white space is displayed. Remember, you may not be able to see the white space on the right hand side. Following the food name print, print the name out three additional times (a total of four times), once normally, and one for each of the three stripping functions lstrip(), rstrip(), and strip().
Answers
Answer:
see the picture
Explanation:
If I am designing an application, which code to I input to create a link
Answers
Answer:
\({ \tt{ < a \: href = url > < a > }}\)
The last must be a closing tag
what are the main components involved in data transmission
Answers
Answer:
connection
Explanation:
connection between each device
What Is Cold Messaging?
Answers
Answer:
Cold messaging is sending prospects messages when they are not primed to listen to you. It’s like sending messages to people who, with a little effort, can turn into your potential clients eventually.
Explanation:
However, there is a very thin line between cold messaging and spamming. The only difference is the target audience. A right cold messaging strategy means sending the right messages to the right people. While spamming means hitting up every profile that comes into the way.
does Anyone here knows introduction programming..
Answers
Answer:
Programming is writing computer code to create a program, to solve a problem. Programs are created to implement algorithms . Algorithms can be represented as pseudocode or a flowchart , and programming is the translation of these into a computer program.
Where should a photographer place lights for a headshot? Headshot lighting is more important with darker backgrounds. The light should be at a 45-degree angle from the subject. The light should be in front of the subject. The third light should be the subject to form a ring of light around the subject’s hair.
Answers
Answer:
Headshot lighting is more important with darker backgrounds. The
(key) light should be at a 45-degree angle from the subject. The
(fill) light should be in front of the subject. The third light should be
(behind) the subject to form a ring of light around the subject’s hair.
Explanation:
i searched it up individually and thats what i got
help with these 2 questions srry for the horrible pic

Answers
Answer:
the first one is email address nd the second one is semi-blocked letters ? sorry if im wrong.
Explanation:
Answer:
I cant read
Explanation:
What is one way a lender can collect on a debt when the borrower defaults?
Answers
Answer:
When a borrower defaults on a debt, the lender may have several options for collecting on the debt. One way a lender can collect on a debt when the borrower defaults is by suing the borrower in court. If the lender is successful in court, they may be able to obtain a judgment against the borrower, which allows them to garnish the borrower's wages or seize their assets in order to pay off the debt.
Another way a lender can collect on a debt when the borrower defaults is by using a debt collection agency. Debt collection agencies are companies that specialize in recovering unpaid debts on behalf of lenders or creditors. Debt collection agencies may use a variety of tactics to try to collect on a debt, including contacting the borrower by phone, mail, or email, or even suing the borrower in court.
Finally, a lender may also be able to collect on a debt when the borrower defaults by repossessing any collateral that was pledged as security for the debt. For example, if the borrower defaulted on a car loan, the lender may be able to repossess the car and sell it in order to recover the unpaid balance on the loan.
Explanation: