You have a system that allows the owner of a file to identify users and their permissions to the file. which type of access control model is implemented?
Answers
The system described in the question is implementing an access control model known as Discretionary Access Control (DAC). In DAC, the owner of a file has the authority to determine who can access the file and what permissions they have.
1. Discretionary Access Control (DAC) is a type of access control model where the owner of a resource has the ability to control access and permissions for that resource.
2. In this case, the owner of the file has the authority to identify users and assign permissions to the file.
This means that the owner can decide which users can access the file and what actions they can perform on it.
3. For example, the owner may grant read-only access to some users, allowing them to view the contents of the file but not modify or delete it. Other users may be granted read and write access, giving them the ability to both view and modify the file.
To know more about Discretionary visit:
https://brainly.com/question/29545895
#SPJ11
Related Questions
in a typical client/server system, the server handles the entire user interface, including data entry, data query, and screen presentation logic. true or false
Answers
In a typical client/server system, the server handles the entire user interface, including data entry, data query, and screen presentation logic. This statement is false.
The client/server system has two distinct parts, which are the client and the server. The client sends requests to the server, while the server receives these requests and processes them.
It is common for clients to request data and for servers to send data to clients. In a typical client/server system, the client provides a user interface that allows the user to interact with the system.
This user interface includes features such as data entry, data query, and screen presentation logic. The client sends requests for data to the server, which then processes the requests and sends the results back to the client.
To know more about server visit:
https://brainly.com/question/3454744
#SPJ11
All information that is to be processed by a computer must first be entered into memory via an input device.
a. true
b. false
Answers
1. DISCUSSION - 90% of adults are older than average All Sections 1515 unread replies.4747 replies. A researcher said that in a certain city, 90% of adults are older than the average age of adults in the city. Discuss whether or not this is possible.
Answers
No, it is not possible for 90% of adults to be older than the average age of adults in a city as it contradicts the concept of calculating an average based on the entire population.
Is it possible for 90% of adults to be older than the average age of adults in a city?It is not possible for 90% of adults to be older than the average age of adults in a city. By definition, the average age represents the sum of all ages divided by the number of individuals.
If 90% of adults were older than the average age, it would mean that the remaining 10% of adults would have to be significantly younger to bring down the average.
However, the average age includes all adults, so it is mathematically impossible for the majority (90%) to be older than the average.
This statement appears to be contradictory or based on a misunderstanding of how averages work.
Learn more about average age
brainly.com/question/18029149
#SPJ11
Former CIA employee and NSA contractor, ____________ is seen by many as either a whistle-blowing hero or a traitorous villain. This person gathered sensitive digital documents from U.S., British, and Australian agencies, and leaked them to the press, exposing the extent of government surveillance efforts.
Answers
Learn more:
Edward Snowden: brainly.com/question/3426041
Which command would you use to evenly distribute your table within the margins of the page?
Answers
Click the Table Layout tab after selecting the columns or rows you wish to be the same size. Select Distribute Rows or column distribution under cell size
How do you add a margin to a table in HTML?Using a::before or::after pseudo-element is another approach to add some margin to a body element. By doing this, we essentially add a new row that is empty and that we can use to add some space before our tbody> items.
What is meant by the layout tab?You can arrange the pages of your document exactly how you like by using the choices found on the Page Layout tab. You can modify page size and orientation, add divisions and line spacing, display line numbers, set section indentation and lines, and define margins. You can even apply themes.
To know more about layout tab visit:
https://brainly.com/question/12684913
#SPJ1
to rank search listings, the algorithm tries to understand the overall value of a webpage. it does this by using feedback from a process that may contain signals, such as links from prominent websites. this represents which results key factor?
Answers
This represents the key factor of "relevance" in ranking search listings based on signals like prominent website links and overall webpage value.
This represents the key factor of "relevance" in ranking search listings. The algorithm aims to understand the overall value of a webpage by analyzing various signals, including feedback from processes like links from prominent websites. By considering these signals, the algorithm determines the relevance of a webpage to a given search query. The more relevant a webpage is deemed to be, the higher it is likely to rank in search results.
Relevance plays a crucial role in search engine algorithms as it directly impacts the quality and accuracy of search results. By evaluating factors like content, keywords, user behavior, and external signals such as backlinks, search engines strive to deliver the most relevant and useful results to users.
By considering feedback from various sources and analyzing signals like links from prominent websites, search algorithms can gain insights into the value and authority of a webpage. These signals help the algorithm determine how well a webpage aligns with the search intent and how likely it is to provide valuable information to users. Ultimately, the goal is to present search listings that are most relevant and useful to the user's query.
Learn more about website:
https://brainly.com/question/28431103
#SPJ11
Create a Single Record form from the Classes table.
Answers
The way to create a Single Record form from the Classes table is that.
The Classes table was selected by a right-click. You selected the More Forms and Form buttons in the Forms Ribbon Group's Create Ribbon Tab.What does class in a table tag mean?A system of record (SOR) or source system of record (SSoR) is a term used in data management to refer to an information storage system (typically implemented on a computer system running a database management system) that serves as the official data source for a specific data element or piece of information.
To use, select the table or query that holds the data for your form in the Navigation Pane, then click Form under the Create tab to start creating a form from that table or query in your database. When using Layout view, Access produces a form and shows it there.
Therefore, One or more classnames are given to the tag through the class property. In a stylesheet or a local file, classnames are defined.
Learn more about Classes table from
https://brainly.com/question/29606486
#SPJ1
The users in your organization bring their own mobile devices to the office and want to be able to access the network with them. You want to protect your network from malware threats that might be on these devices. You want to make sure these devices meet certain requirements before they can connect to the network. For example, you want them to meet the following criteria: Hardware and Windows startup components are clean. The kernel is not infected with a rootkit. Boot drivers are clean. Which Windows feature can you use to protect your network from malware threats that might be on your users' mobile devices
Answers
Answer:
The Windows feature that can be used to protect a network from malware threats that might be on the network user's mobile devices is;
Device Health Attestation (DHA)
Explanation:
Device Health Attestation (DHA) is a feature introduced in version 1507 of widows 10 that enables increased security of the network of enterprises to have mainly hardware which are attested and monitored using cloud based service health check or DHA service on Windows Server 2016.
Device Health Attestation carries out assessments on devices based on Windows 10 devices and Windows 10 mobile devices that work with TPM 1.2 or 2.0 and devices which are within the premises
Items checked include boot configuration and attributes such as Secure Boot, ELAM, and BitLocker
Corrective action are triggered by Mobile Device Management (MDM) based on report data from the DHA.
Can you explain that how these codes convert data to binary please ?
void send_byte(char my_byte)
{
digitalWrite(LED_PIN, LOW);
delay(PERIOD);
//transmission of bits
for(int i = 0; i < 8; i++)
{
digitalWrite(LED_PIN, (my_byte&(0x01 << i))!=0 );
delay(PERIOD);
}
digitalWrite(LED_PIN, HIGH);
delay(PERIOD);
}
Answers
The given code is used to send a byte of data over a communication channel in the form of binary data. It does this by converting the byte to its binary equivalent, and then transmitting the individual bits one at a time. Let us understand how this code converts data to binary:
The send_byte() function takes a single argument, which is a character representing the byte of data that needs to be transmitted. This byte is passed to the function as an 8-bit character, and it needs to be transmitted as 8 separate bits. The first thing that the code does is to turn off an LED that is connected to the LED_PIN. It then waits for a short period of time, represented by the PERIOD variable. The code then enters a for loop that will run 8 times. This loop is used to transmit the 8 bits that make up the byte. For each iteration of the loop, the code checks the value of a single bit in the byte.
The bitwise AND operator (&) is used to check the value of the bit. The bit is extracted using the left shift operator (<<), which shifts a value to the left by a certain number of bits. In this case, the operator is used to shift a 1 to the left by i bits, where i is the current iteration of the loop. If the value of the bit is 0, the LED is turned off. If the value of the bit is 1, the LED is turned on. After each bit is transmitted, the code waits for another period of time. The code then turns on the LED to signal the end of the byte transmission and waits for another period of time. This completes the transmission of a single byte of data in the form of binary data.
To know more about binary data refer to:
https://brainly.com/question/13371877
#SPJ11
Consider the following code segment.
int[][] mat = {{10, 15, 20, 25},
{30, 35, 40, 45},
{50, 55, 60, 65}};
for (int[] row : mat)
{
for (int j = 0; j < row.length; j += 2)
{
System.out.print(row[j] + " ");
}
System.out.println();
}
What, if anything, is printed as a result of executing the code segment?
A 10 15 20 25
50 55 60 65
B 10 20
30 40
50 60
C 10 15 20 35
30 35 40 45
50 55 60 65
D Nothing is printed, because an ArrayIndexOutOfBoundsException is thrown.
E Nothing is printed, because it is not possible to use an enhanced for loop on a two-
dimensional array.
Answers
Answer:
C
Explanation:
10 15 20 35
30 35 40 45
50 55 60 65
pulsed laser technology called lidar to detect and monitor the environment is an integral part of .
Answers
Pulsed laser technology called lidar to detect and monitor the environment is an integral part of Self-driving trucks.
What type of laser is LiDAR?Topographic and bathymetric lidar are said to be of two different types. While bathymetric lidar also measures elevations of the seafloor and riverbeds using water-penetrating green light, topographic lidar typically maps the land using a near-infrared laser.
Therefore in regards to self-driving vehicles, self-driving trucks, sometimes referred to as autonomous trucks or robo-trucks, operate without a human driver. Self-driving semi trucks are being tested by many businesses. Similar to self-driving vehicles, self-driving trucks, sometimes referred to as autonomous trucks or robo-trucks, operate without a human driver.
Learn more about Self-driving trucks from
https://brainly.com/question/22527873
#SPJ1
PLEASE HURRY!!!! Look at the image below!

Answers
Answer:
print()
The print() function prints the programs message to the screen, or other standard output devices, I hope that this helps (◠‿◠)
Answer: i think it is input
Explanation:
because the word input means to put in something or operate
which item can be added to outlook messages, like a word document or powerpoint presentation, that takes standard bulleted lists and provides the ability to integrate graphics and text? chart table smartart wordart
Answers
The item that can be added to Outlook messages, like a Word document or PowerPoint presentation, that takes standard bulleted lists and provides the ability to integrate graphics and text is called SmartArt.
SmartArt is a feature in Microsoft Office applications, including Outlook, that allows users to create visually appealing diagrams, charts, and other graphical representations. SmartArt provides a variety of pre-designed layouts that users can choose from and customize to suit their needs. One of the key benefits of SmartArt is that it allows users to quickly and easily present complex information in a way that is easy to understand and visually appealing. With SmartArt, users can create professional-looking graphics that can enhance their Outlook messages and other Office documents.
Learn more about SmartArt here;
https://brainly.com/question/14194323
#SPJ11
Which Excel IF function is not in the correct syntax?
= IF(A4<=250, 1, (IF(A4>250, 2, "MidPoint")))
= IF(B18=1, A18, 500-A18)
= IF(B18, A18, 500-A18)
= IF(A4<=250, 1, (IF(A4>250, 2, D5)))
Answers
The Excel IF function which is not in the correct syntax is: = IF(A4<=250, 1, (IF(A4>250, 2, D5))).
What is Microsoft Excel?Microsoft Excel can be defined as a software application that is designed and developed by Microsoft Inc., for analyzing and displaying spreadsheet documents by using rows and columns in a tabulated format.
The types of function in MS Excel.In Microsoft Excel, there are different types of functions that are called predefined formulas and these include the following:
Average functionMinimum functionSum functionMaximum functionCount functionIF functionIn this scenario, the Excel IF function which is not in the correct syntax is: = IF(A4<=250, 1, (IF(A4>250, 2, D5))) because A4 is referencing two different inequalities (values).
Read more on Excel formula here: brainly.com/question/26053797
#SPJ1
why is it important to make sure link is from a trusted source? can't we just click and if it's not what we want or
through it would be just go back?
Answers
Answer:
First... you don't want to have to click on a million different sites
Second.... some sites have viruses, and they activated when you click on a certain source.
Explanation:
Hava great day!
Answer:
They say that it has to be from a trusted source because, you will be needing the correct and trustworthy information. Like take wikipedia for example anyone can go on there and change the information to something fake and then you have fake info in what you are writing.
Explanation:
a a a a I don't need help!?
Answers
Answer:
ok
Explanation:
ok
help plz ASAP :)
only for smart ppl ;)

Answers
Answer:
Cellphone, GPS, and Internet.
Explanation:
I don't quite the understand the question, but...
Hope this helps!
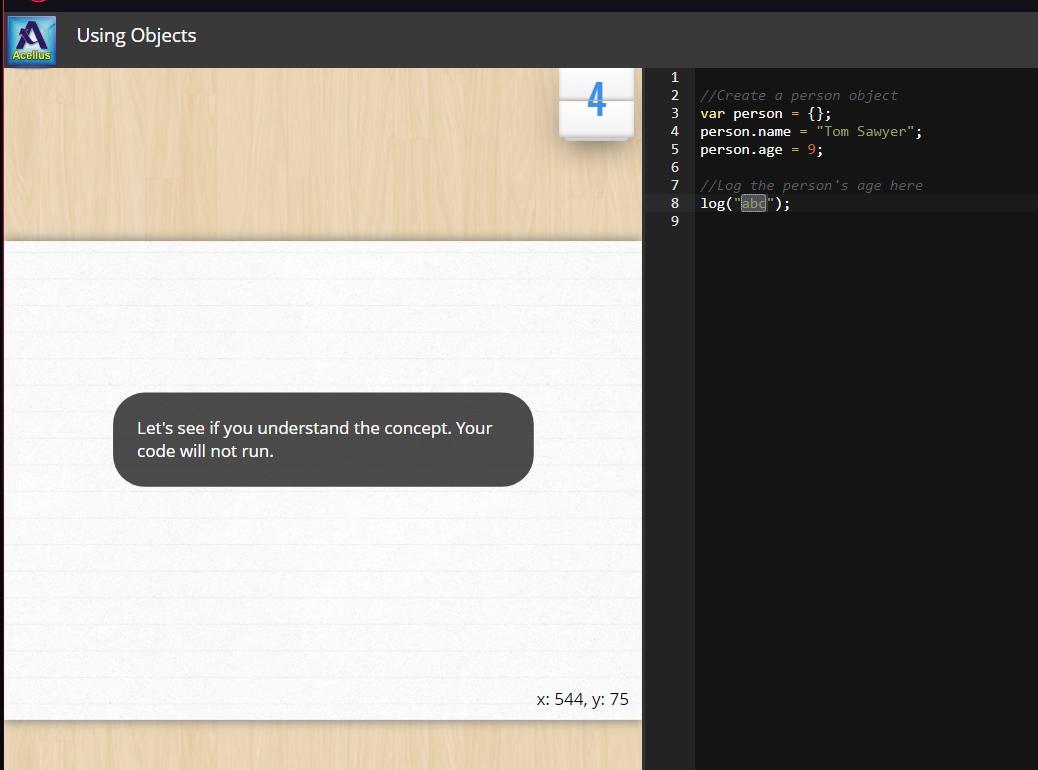
log the 'age' property of the 'person' object
Answers
Answer:
vauwnwkwiauauwiajhwbwbw
Use the Document Inspector to remove all comments and annotations and personal information and hidden information from this workbook. Close the Document Inspector when you are through.
Answers
The Document Inspector is a feature in Microsoft Office applications such as Word, Excel, and PowerPoint.
How to use the document inspectorTo remove comments, annotations, personal information, and hidden information from a workbook, you can follow these general steps:
Open the workbook in Excel.
Click on the "File" tab in the top left corner of the screen.
Click on "Info" in the left sidebar.
Click on "Check for Issues" in the right sidebar.
Click on "Inspect Document."
In the Document Inspector dialog box, select the checkboxes for the types of information you want to remove.
Click "Inspect."
Review the results of the inspection and click "Remove All" for each type of information you want to remove.
Save the workbook with a new name to preserve the original, if desired.
Note that the specific steps may vary slightly depending on the version of Excel you're using.
Read more on Document Inspector here:https://brainly.com/question/30597777
#SPJ1
If one of the resistors is turned off (I.e. , a light bulb goes out), what happens to the other resistors (light bulbs) in the circuit? Do they remain on? (I.e., lit)?
Answers
Answer:
No, they don't remain on because If any of bulbs in a series circuit is turned off from its socket, then it is observed that the other bulbs immediately go out. In order for the devices in a series circuit to work, each device must work. If one goes out, they all go out.
In azure backup, which type of vault is recommended for better protection?
a) none of the options
b) both the options
c) the backup vault
d) recovery services vault
Answers
In Azure Backup, the recommended type of vault for better protection is:
d) Recovery Services Vault.
The Recovery Services Vault is specifically designed to provide a comprehensive backup and restore solution in Azure. It offers advanced features and capabilities for protecting and managing data across various Azure services and resources.
By using a Recovery Services Vault, you can centrally manage and configure backup policies for virtual machines, Azure Files, SQL databases, Azure VM workloads, and other supported data sources. The vault provides a unified interface and control plane for managing backup and recovery operations.
Some key features and benefits of the Recovery Services Vault in Azure Backup include:
Backup policy management: You can define and customize backup policies to schedule backups, set retention periods, and specify backup frequency according to your specific requirements.
Application-consistent backups: The Recovery Services Vault ensures that backups are created in a consistent state, allowing for reliable recovery of applications and data.
Incremental backups: It enables efficient storage usage by performing incremental backups, only capturing changes made since the last backup, which reduces backup duration and storage costs.
Long-term retention: The vault supports long-term retention, allowing you to retain backups for extended periods as per compliance or regulatory requirements.
Disaster recovery: In addition to backup, the Recovery Services Vault can also facilitate disaster recovery scenarios by replicating and orchestrating the failover of workloads across Azure regions.
Therefore, to achieve better protection in Azure Backup, it is recommended to use the Recovery Services Vault (option d).
Learn more about azure backup here, https://brainly.com/question/30316099
#SPJ11
Geraldo would like to compare two areas of text, Text1 and Text2, to each other. What steps should he take?
od
select Text1, hit F1, click. "Compare to another selection," select Text2
select Text1, hold Shift+F1, click "Compare to another selection," select Text2
hold Shift+F1, select Text1, hold Shift+F1 again, select Text2
Ohit F1, select Text1, hit F1 again, select Text2
Answers
a computer administrator sets up a client workstation to join a centrally managed network. in windows, what options should the administrator configure to do this?
Answers
To set up a client workstation to join a centrally managed network in Windows, the computer administrator should configure: Network Settings, Domain or Workgroup, System Properties, Group Policies.
Network Settings:
Ensure that the workstation is connected to the network and has appropriate IP settings configured. This includes obtaining an IP address through DHCP or assigning a static IP address if required by the network.Domain or Workgroup:
Determine whether the needs to join a domain or a workgroup. If it needs to join a domain, the administrator should specify the domain name and provide appropriate credentials with administrative privileges.System Properties:
Open the System Properties dialog by right-clicking on "This PC" or "My Computer," selecting "Properties," and navigate to the "Computer Name" or "Advanced System Settings" section. From there, click on "Change" to modify the computer's domain or workgroup membership.Group Policies:
If the centrally managed network utilizes group policies for security and configuration management, ensure that the client workstation is configured to receive and apply those policies. Group policies can be managed through the Group Policy Management Console (GPMC) or Active Directory.To learn more about workstation: https://brainly.com/question/30206368
#SPJ11
What are some ways you can make a good impression on a client, and how would you respond to a difficult client situation?
Cybersecurity~
Answers
Not that you can make a good impression and win clients by being knowledgeable, professional, and responsive. Respond to difficult client situations by remaini ng calm, listening actively, and working to find a solution that addresses their concerns.
What is the rationale for the above response?Making a good impression on a customer is critical in the realm of cybersecurity in order to develop trust and confidence in your skills. One method to do this is to be well-versed on the numerous cybersecurity dangers and solutions applicable to the client's business or company.
Also , being professional and receptive to their wants and concerns might aid in the development of trust. It is critical to remain calm and not become defensive in the face of a challenging client situation.
Instead, actively listen to their problems and collaborate to create a solution that meets their requirements.
Learn more about Winning Clients:
https://brainly.com/question/28769079
#SPJ1
Which of the following is the best example of an installation issue?
A computer can’t find the file that it needs to perform an operating system function.
A computer displays error messages, and then the Blue Screen of Death appears.
A user made an error while trying to set up a software program.
A software program is not compatible with the computer’s operating system.
Answers
The option that is the best example of an installation issue is A computer can’t find the file that it needs to perform an operating system function.
What is installation issue?This is known to be a kind of situation in terms of computing where one is unable to carry out a task as a result of missing item or code.
Note that The option that is the best example of an installation issue is A computer can’t find the file that it needs to perform an operating system function.
Learn more about installation from
https://brainly.com/question/10012411
#SPJ2
What type of business document is used to
communicate inside the company?
Answers
Answer:
Where’s your answer choices
Explanation:
Put it in the comments and I’ll do the same
Which of the following would be the most important technical skill for a camera operator interested in embedding with the military? ONLY ANSWER IF 100$ RIGHT WILL THROW IN $$$ IF I GET AN A
mounting a gear head tripod
night-time camera operations
capturing live action shots
setting up a dolly track
- Another question
Which of the following could have the most significant impact on the future process of technology innovation?
increased free market structures
increased competition between software developers
increased Internet regulations
increased Internet deregulations
Answers
Answer:
question 2 is B
Explanation:
i am still figuring out the first one
69.147.76.15 is an example of what?
Answers
Answer:
IP address.
Explanation:
An IP address is an acronym for internet protocol address and it can be defined as a unique number assigned to a computer or other network devices, so as to differentiate each device from one another in an active network system. Thus, an IP address is typically used to uniquely identify each computer or network devices connected to the internet or network.
Hence, 69.147.76.15 is an example of an IP address.
In Computer networking, IP address are classified into two (2) main categories and these are;
1. Local (internal) IP address.
2. Global (external) IP address.
Generally, when this IP address such as 69.147.76.15 is translated by a domain name system (DNS), it is mapped to the domain name yahoo.com which is much more understandable or comprehensible to the end users.
What are the common internal components to most electronic devices?
Answers
Answer:
RAM, ROM, CPU, Capacitor, Resistor, Relay.
What are characteristics of fluent readers? Check all that apply. reading known words automatically pronouncing words correctly reading words as quickly as possible understanding the meanings of the words being read O looking up all unknown words in the text being read
it's A,B,D
Answers
Answer:
D,A,B hope this is it!!!!!
Answer:
The person above me is correct
Explanation: credit to him